A ‘Codec’ Moment
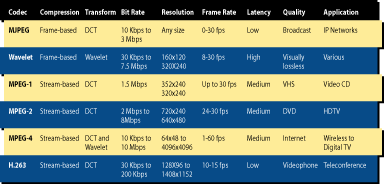
Video compression through codecs is the process of reducing the number of bits needed to represent a given set of data. Compression works by eliminating redundancies in the raw data. In video encoding, further compression can be achieved by reducing detail, color, size and luminescence from the video signal
Basics of compression
Codecs reduce the space required to store video and, more importantly, reduce the bandwidth needed to transmit it across a network. This reduction is critical because raw video files are extremely large. A relatively small number of cameras delivering uncompressed video can quickly overwhelm even the most robust networks and storage systems. Video compression is required simply to make network video viewing, storage and management feasible.Frame-based codecs employ intra-frame compression using a mathematical algorithm acting on pixels within the frame. The two most common frame-based codecs are MJPEG and Wavelet. Frame-based codecs are preferred for many security applications because each frame represents only data that is collected at that single point in time. This can make them more appropriate for forensic purposes, where the viewer is studying each individual frame for information.
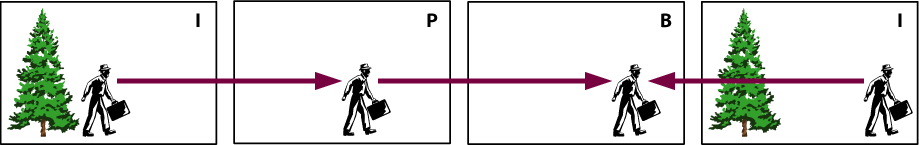
Stream-based codecs employ algorithms that encode one complete frame at a specified interval, and then encode the inter-frame differences of subsequent frames for the balance of the interval. Decoders then decompress each key frame and use the difference information to recreate the subsequent frames until the next key frame is reached. Examples of stream-based codecs are MPEG-1, MPEG-2 and MPEG-4.
Stream-based codecs are popular for applications where smooth motion is important for live viewing of the video and network capacity is limited. The disadvantage of stream-based codecs is that they often have minimum bandwidth requirements. If bandwidth drops anywhere on the network, the video can become unusable. Stream-based codecs also introduce additional latency into the system, as multiple frames need to be cached and processed before video is displayed. Finally, stream-based codecs are sometimes considered less appropriate for forensic purposes because they have the characteristic of combining information from different frames and different points in time to build an interim frame that represents only what should be happening at that point.
For high frame rate video on high bandwidth networks, MPEG-2 can be a viable choice. MPEG-2 delivers very smooth motion and is more efficient than MJPEG at high frame rates. It is useful in command and control applications where video is displayed on large screens and video quality is important. MPEG-4 is also beginning to emerge as a useful encoding technique, particularly for wireless and other low bandwidth networks. MPEG-4 will eventually support a wide range of quality/bandwidth choices and may replace MPEG-2 in many surveillance applications.
Some vendors offer proprietary codecs with a variety of performance claims and rationales. While this approach may work in a standalone system like a digital video recorder, network-based video applications should be built using industry-standard codecs. The advantages of multiple suppliers, reduced cost, future expansion capabilities and compatibility with other systems far outweigh any claimed performance gain from a proprietary system.
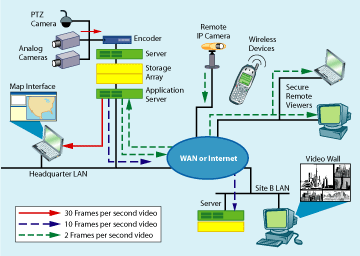
When looking for video distribution platforms, security equipment end users as well as their systems integrators and consultants should look for systems that allow them to work with multiple industry standard codecs that support a full range of applications, such as broadcast-quality video to a command center, remote monitoring over the Internet and access to video through wireless Web-enabled PDAs. An open system architecture based on industry standard codecs allows systems to evolve over time, taking advantage of new technologies as they become available.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





