Channeling RFID
The Department of Homeland Security (DHS) has already adopted RFID in several applications, but Homeland Security’s testing every tech approach.
To fend off the critics, RFID industry executives counter that the problem is that technology can do too many things.
These executives could be right.
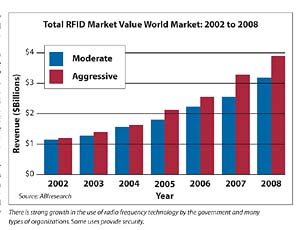
Radio frequency identification applications are quickly branching out of traditional roles and taking on greater importance by security buyers, chief information officers, logistics managers and even brand managers. The growth is stimulated by wartime investment in military logistics technology and a push for supply chain visibility, says ABI, the Oyster Bay, N.Y.-based technology market research firm. ABI estimates the global RFID market will grow to more than $3.1 billion by 2008.
Public and Private Use
The U.S. Department of Defense is only one of many organizations to dramatically increase RFID spending in the last year. As the military found in both Iraq and Afghanistan, the reasons to invest in RFID and other tracking technologies are clear.However, the business cases can be made now that standards are finally materializing, innovations in manufacturing are driving prices down, and software, hardware and integrators of the two are working together to develop cohesive, compatible enterprise solutions.
According to ABI, asset, security and supply chain management application revenue will grow from 20 percent to 48 percent of this projected market.
Initially, asset control, asset tracking and container and pallet-level supply chain management will propel the RFID market. “But as indicated by the proliferating interest among the world’s largest retailers, including Wal-Mart, Metro AG, Carrefour, Tesco and Ahold, item-level tracking in the supply chain is no more than three to four years from widespread implementation,” explains Erik Michielsen of ABI.
A Global Approach
With RFID tags built into products, packages and pallets at the point of manufacture, security officials tasked to protect the assets will potentially piggyback on the technology with new-generation security systems.The bottom line: the enabling of total supply chain visibility through a global information and security network where automated technologies can interoperate and communicate.
That’s the vision of research at the Massachusetts Institute of Technology’s Auto-ID Center of Cambridge, Mass. A recent Auto-ID Center project, in partnership with Savi Technology of Sunnyvale, Calif., and Matrics Inc. of Columbia, Md., shows the promise and the potential controversies of more fully-implemented RFID solutions.
In a move that augments the recent drive by major retailers such as Wal-Mart to track individual products in real-time, Savi, Matrics and the MIT Auto-ID Center are collaborating to embed RFID systems throughout the supply chain. Called “nested visibility,” their integrated solution will help to bridge visibility gaps in the supply chain through use of passive RFID labels to track items and active RFID tags with longer read ranges that track conveyances ranging from pallets and cargo containers to truck trailers and rail cars. When linked with Web-enabled software, makers, marketers, security, inventory, wholesale, transportation, government and retail officials can track an unlimited variety of items. The system can track and identify whole shipments, metal containers or even specific items missing from containers as well as the specific time that security breaches of the container itself occur.
The key to the approach is that there is seamless communication among such system elements as Electronic Product Code (EPC), passive tags and active tags.
Source Tagging
A new-wave step-up from the Universal Product Code, a printed approach, the EPC is an emerging standard developed by the Auto-ID Center for item-level identification and tracking throughout the supply chain. A number of major retailers are sponsoring and supporting the EPC for item-level tracking. Wal-Mart, the world’s largest retailer, will require its top 100 suppliers to have EPC-compliant tags on pallets and cases by the year 2005.Retail loss prevention directors for years have embraced the concept of source tagging of products and packages so they can cut down on the cost of applying anti-shoplifting tags at their warehouses or in-store. On individual and small group level, manufacturers, ranging from shoemakers to CD makers, are source tagging. The problem here is two-fold: the current approach is most often limited to only in-store security needs and the tags most often do not have the ability for tracking, locating and updating electronically.
The newer approaches in testing stages or under development tend to view RFID more globally as a way to track things end-to-end and top-to-bottom.
“To achieve such total supply chain visibility and security worldwide, it’s critical to have a common set of standards for seamless transitions between technologies, processes and borders,” says General (U.S. Army, Ret.) John Coburn, chairman of the Strategic Council on Security Technology, a global advisory resource.
Today, there are numerous RFID security applications on a more limited scale.
For example, the Fort McPherson Army Base in Atlanta, has a test of a new security system based in part on technology from Intermec of Everett, Wash. The system uses Intermec’s Intellitag RFID technology integrated with intelligent gate controller and access control software to enhance vehicle and personnel screening efforts of military policemen at the installation’s gates. The package also allows controlled access to specific internal areas without an increase of manpower, further securing the post.
Matching Cars and People
In this design, Intellitag RFID-enabled windshield decals are assigned and affixed to all vehicles authorized to enter the base. Each tag mounts in the upper portion of the driver’s-side windshield and is coded based on the vehicle owner’s need for access. The gate controller software allows access only to those specific areas. The system can program for multiple options and levels of security access and can adjust to increase security levels under special circumstances, such as specific dates and times or threat levels.Earlier this year, security officials used RFID technology at the 75th Academy Awards. At the event, RFID from Dallas-based Texas Instruments helped provide access control to verify the identity of attendees at strategic perimeter locations and interior checkpoints and restricted access areas.
As part of an overall security framework implemented by Security Solutions, a systems integrator from Los Alamitos, Calif., the nearly 11,000 authorized attendees, guests and staff wore an ID card, issued in advance of the event, which contained a TI-RFid 13.56 MHz smart label. The ID cards also had other embedded high-technology features to facilitate visual screening and identification.
Identifying Celebrities
Five-foot tall kiosks containing a computer monitor, RFID reader and encased computer server were placed in strategic locations at the Kodak Theater. When guests arrived, their identities were verified as they passed through a checkpoint. Additional security checks helped personnel determine who had access to a particular area, such as award presenters needing backstage access. Within one half second of the card being read at the kiosks, security personnel had access to information about the cardholder, including a photograph, name, physical descriptors, security clearances and the date and time the credentials were active.RFID tags are also invading the textile rental and dry cleaning industry.
Texas Instruments' 13.56 MHz RFID tag is an ultra-thin, 22mm circular transponder, housed in plastic. It is fully compatible with the ISO 15693 standard and has been designed and tested to withstand the harsh industrial cleaning process. Sewn into or attached to textile items, TI-RFid tags provide more accurate identification and greater accountability as well as improve handling through each stage of cleaning and processing to final customer delivery.
The Laundry Transponder provides a unique, 64-bit factory-programmed ID, which cannot be duplicated, ensuring that no items are misidentified. With 2,000 bits of memory, the transponder, available in a read/write format, can be programmed with both user and application-specific information. The transponder’s unique ID can also be laser-etched on the plastic casing for visual identification. Up to 50 transponders per second can be simultaneously identified by an RFID reader/antenna with no line-of-sight required. TI also manufactures a variety of 13.56 MHz, ISO 15693 reader/antennas and partners with software developers and systems integrators to provide textile rental and dry cleaning customers with a turnkey RFID solution. “As a pioneer in 13.56 MHz technology, TI has deployed more than 250 million tags worldwide in a range of RFID applications, including inventory management and supply chain,” says Bill Allen of Texas Instruments RFid Systems. “We’re bringing our wealth of experience to the textile rental and dry cleaning industry with a product specifically designed for a harsh and demanding cleaning environment.”
SECURITY magazine covers radio frequency identification technology on a daily basis on the magazine’s Web site at www.securitymagazine.com. Click on the DAILY NEWS service and you can access scores of news, technology journal and government research articles on RFID as well as other source tagging and security technology issues.
SIDEBAR 1: Tuning into RFID
Radio frequency identification systems include two types of tags: active and passive.In the active version, the tag broadcasts data to readers. They have batteries and are larger and more expensive than passive tags.
In the passive version, the tag gets its juice from the reader.
There are security applications that, depending on need, can use one or the other versions.
Tags can come in numerous modes ranging from those printed on wristbands and baggage tags to large-sized assembled models. The size of the tag often determines the read range.
Prices continue to fall for many versions of the tags, leading many to point to growth in mass-market applications.
However, at a debate at this year’s RFID World Conference, industry experts took sides on the hype versus reality of the low-cost, high-volume RFID tags. Ultimately all agreed that the issue is not the cost but rather the business value and opportunities created by the technology. “My advice is to stop worrying about the penny tag. It’s simply not relevant,” implored one panelist. “Rather than waiting for tag prices to drop,” manufacturers and end users alike should focus on developing the business rules for collaboration and the use of real-time data in security, supply chain and inventory management.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!




