Building Princeton’s Defense

The proliferation of increasingly strategic and sensitive networked equipment at remotely managed sites, including those where managers or supervisory personnel are occasionally offsite, has intensified the need to assure protection against such seen and unseen intruders.

Monitoring and management
One solution is to provide comprehensive remote monitoring and protection using a network peripheral device. Such devices must provide the right combination of monitoring and management capabilities, integrating multiple existing inputs into an SNMP trap alarm system that delivers immediate notification via the network’s native protocol. Such a project can be driven by executives representing facility, security and logical security.Chartered in 1746, Princeton was the fourth college established in British colonial America. Last year the university enrolled 4,635 undergraduate and 1,997 graduate students at its 500-acre campus located in Princeton, N.J. The faculty of approximately 1,000 includes recipients of the Nobel Prize in physics, literature, economic sciences and medicine. All faculty members are expected to teach as well as engage in scholarly research.
Like other universities and research centers, Princeton has a need to protect the intellectual property. This includes securing facilities that house expensive equipment and sensitive data.
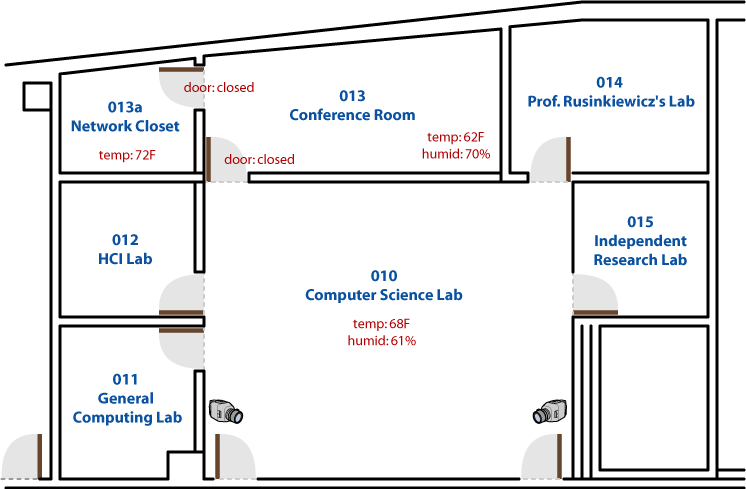
“Normally, the support staff members are offsite during nights and weekends,” said Chris Tengi, systems and network administrator at the university’s Department of Computer Science. “But we are always concerned about power supply, humidity, ambient temperature and related equipment that supports our facilities. If we have some sort of mishap that knocks out air conditioning in the middle of the night, we need to know about it.”

“The threats we encounter are mostly heat and humidity,” said Tengi. “Although we are certainly concerned about unauthorized entry or human actions that can compromise our systems.”
In fact, one of the department’s major investments in physical monitoring and protection equipment was in motion-activated security cameras (AXIS Communications, Chelmsford, Mass.), which are mounted facing outside entries of the Computer Science Building as well as the main computer room. But while the cameras addressed the need to detect and monitor human activity after hours, an integrated solution to monitoring and managing heat- and humidity-related situations was still needed.
Concerned about the prospects of system problems due to human or environmental impediments, Tengi investigated the SNMP-Link Model SL61 Remote Site Manager made by Omnitronix.
Based in Seattle, Omnitronix data collection devices includes site-management product line which grew out of experience in PBX alarm management and remote equipment access, especially for SNMP systems.
These devices typically monitor critical business equipment – phone systems, power supplies or communications/networking components – as well as the physical conditions that impact the health of such equipment. They then provide the network interface and intelligence required to get such non-networked devices into the control of the network.
With the SL61, in particular, as many as 16 different EventSensors that monitor temperature, humidity, airflow and noise, for example, can be daisy-chained for connection to Ethernet, phone line, Internet or wireless systems.
The integration process
Tengi acquired three of these self-contained units for three separate Computer Science rooms and connected sensors that monitor heat, humidity and door activity to each unit.“We used the event sensors to send SNMP traps so that if they detected high humidity or temperatures that are too high or too low, the corresponding trap will generate an e-mail message to our pagers,” said Tengi. “You can buy and configure these with different combinations of capabilities. So, if I only needed a temperature sensor in one place and I didn’t need to detect contact closure or humidity conditions, I can do just that. Being able to mix or match the sensors is convenient and saves on costs.”
Tengi also installed an Omnitronix SL10, a low-cost SNMP-Link, to monitor the environment in an additional lab.
Improved monitoring
Tengi noted that accidental environmental problems resulting from human intervention are now handled by the event sensor system. For example, since some of the computer lab facilities were previously standard office spaces, the air conditioning thermostats are accessible by occupants.“If they feel the room is too cool, they raise the thermostat, but if they leave the room that way, it will get too hot for the equipment,” Tengi points out. “But now the sensors will detect the temperature rise at whatever threshold we have set and we can make corrections before the equipment is affected.”
In another instance, sensors detected when a maintenance crew entered the computer room out of hours to borrow a power outlet, disconnecting some equipment in the process. “The system notified me on my pager, so we were able to take care of the problem before any damage occurred,” said Tengi. “We then reviewed the images generated by the motion-detector-activated cameras, and we could see that the cleaning crew had unplugged our equipment by mistake.”
Also discussed is the possibility of integrating other devices, such as the surveillance cameras, with environmental event sensing capabilities.
“We purchased the motion detectors for the cameras before we installed the SL61s,” said Tengi. “But you can wire the cameras and configure them in such a way that when a contact closure on a door trips the SL61, it could trigger a camera to take pictures.
“We didn’t take advantage of all the features,” said Tengi, “but if we need other capabilities in the future we can simply order event sensors accordingly. For our application, getting the SNMP query capability without having to buy an SL61 for every location – and the flexibility of being able to put sensors in different configurations depending on what you need – all adds to the value of the basic device.”
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







