Information Security Top-Down
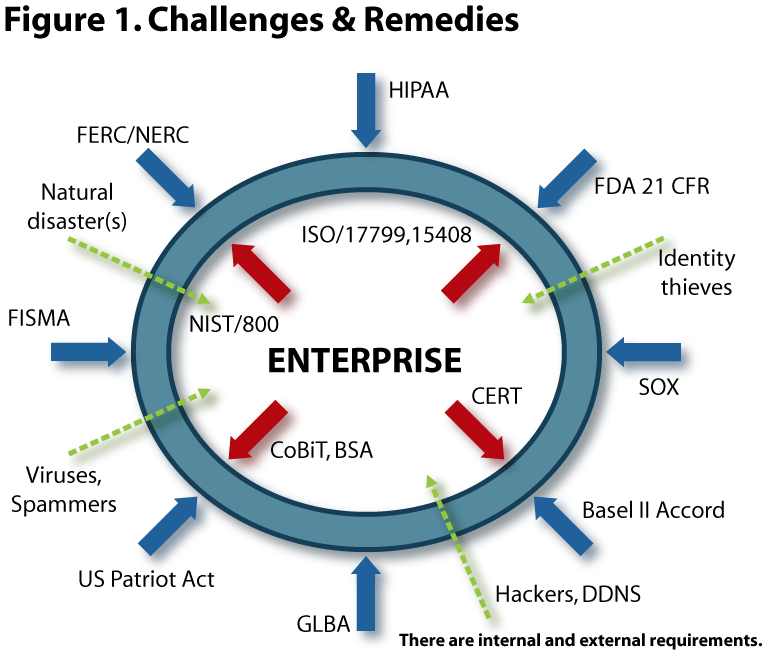
Challenges and remedies
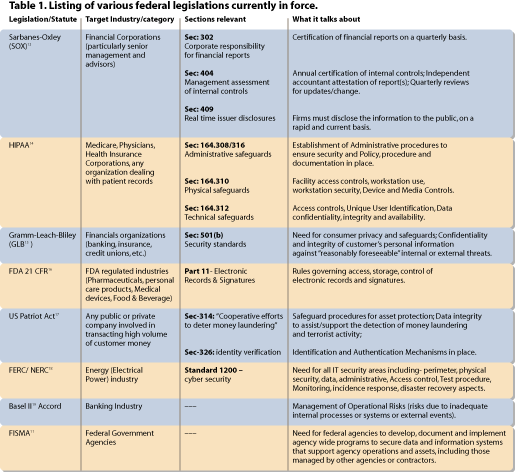
Many private9,10, academic8 and federal initiatives11 are trying to address the growing needs and challenges faced by the enterprises. Each initiative differs in its objective, scope, comprehensiveness and target audience. Some are simple policies and procedures, others are more comprehensive recommendations and best practices9,10,11,12. The laws listed in Table 1 demonstrate that privacy of user data, information confidentiality, integrity and availability of data or service and means to realize them are the central demands. While some legislation requires extensive confidentiality mechanisms to be put in place, others emphasize data availability and other operational procedures. Enterprises that fall in one of the regulated categories will need to have the infrastructure and mechanisms in place to guarantee compliance. Having identified the reasoning, remedies and repercussions associated with information security, enterprises need to develop due diligent practices and programs. Figure 1 is the scenario; Tables 1 and 2 enumerate the requirements.Bottom-up vs. top-down approach
Organizations have dealt with the problem of security management through varied means. Traditionally, enterprises have adapted a bottom-up approach, in which operational staff initiate the process then propagate their findings upward to management as proposed policy recommendations. As management has no information on what is the threat associated, its implications, idea on resource allocations, possible return and method to implement security, this approach has at times sparked a fiasco.
On the contrary, a reverse look on the entire issue, the top-down approach is proving to be highly successful. Here, management understands the seriousness and initiates the process, which is then systematically percolated down to operations staff.
Executive management
The top-down approach begins with management establishing a framework for initiating and implementing security practices in the enterprise. Management can consult the Federal Information Security Management (FISMA) and ISO 17799 standard. FISMA highly emphasizes the need for management hierarchy and a delegation of roles. Though it has been at federal agencies, it can help private enterprises too. ISO-17799 can help in implementing a security program throughout an organization. As an inherent duty of the executive, controlling costs and devising a strategy to maximize return represents a paramount objective. To meet this objective, management must align their business objectives with the recommendations of new standards. Methodologies8 such as the Security Attribute Evaluation Method, developed by Carnegie Melon University, and fault tree analysis can help to perform cost benefit analyses and risk assessment studies. Such methods can help to choose one security architecture over another.
Security policies and procedures are the starting point of establishing a central security initiative.
Operations
Mainly constituted by physical administrative and technical security, the operations layer ensures secure operation of the components integrated into an infrastructure. Disaster recovery procedures5, business continuity planning, remote backup facilities, secure integration of application, middleware, back-end-layers and documentation of various infrastructure elements have to be in place to meet operational security and continuity. The National Institute of Standards and Technology (NIST)10 and CERT8 have published several guidelines and checklists to address this layer’s requirements.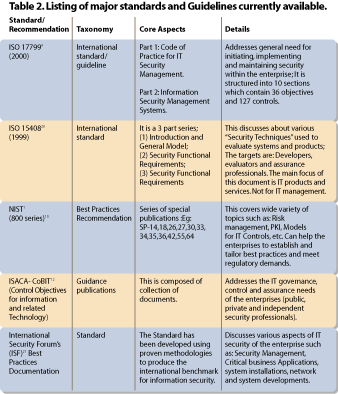
Technology
Enterprises build and acquire solutions to accomplish their business goals and processes. Recently the trend is shifting towards procuring commercial, off-the-shelf products (COTS)22. Many federal regulations, including FISMA, strongly recommend that agencies consider purchasing pre-made integrated software for regulatory compliance from large software vendors.
Security metrics are essentially the processes and tools for facilitating upper management in decision making about performance, accountability and reporting processes associated with the security program. An effective security metrics program in an enterprise provides useful data for allocation of resources. A structured existence of the program in a top-down approach is a prerequisite for any metrics program. An NIST10 (800-55) guide entitled Security Metrics Guide for Information Technology Systems discusses the components of an organizational metrics program and the means to accomplish it. The information gathered from various layers is used as input to the metric program and, in turn, provides input for upper management to translate investments into a comprehendible return.
Framework and security model based approach
Recently, the Business Software Alliance23 observed that a top-down approach would be ineffective unless there was a “governance framework” in place in the upper layers that defined roles and delegated responsibilities within the management structure. FISMA also strongly emphasized the importance of team members knowing where responsibilities lay.
Such a framework can accelerate progress and increase management’s accountability, as discussed in PricewaterhouseCoopers’24 paper titled Excellence in Security. The Information Systems Audit and Control Association12 published its collection of documents concerning governance and control objectives as an online resource dubbed “CoBIT”12.
Conclusion
Companies small and large all have to lay out a clear roadmap and coherent infrastructure for their security needs. Following due diligence not only can sustain a business and protect it, it can also prepare the enterprise for future compliance needs. Treat security more as a governance issue than a technology issue.References
1. http://cybercrimes.net/Terrorism/terrorism.html
2. www.spammingbureau.com
3. www.consumer.gov/idtheft/
4. IT Security Technologies Can Address Regulatory
Compliance by Gartner Inc. (Feb, 2004)
5. http://secinf.net/disaster_recovery
6. The Definitive Guide to Identity Management
from Rainbow Technologies Inc.
7. HIPAA Privacy, Security and Legal
Implications at www.rx2000.org
8. www.cert.org
9. www.iso-17799.com
10. www.nist.gov
11. FISMA resource at www.chips.navy.mil
12. http://isaca.org
13. www.sarbanes-oxley.com
14. www.hhs.gov/ocr/hipaa
15. www.ftc.gov/privacy/glbact/glb-faq.htm
16. www.fda.gov/ora/compliance_ref/part11/
17. www.epic.org/privacy/terrorism/hr3162.html
18. www.ferc.gov/legal/ferc-regs.asp
19. www.bis.org
20. www.iso-standards-international.com/
21. The standard of good practice for Information
Security, www.securityforum.org
22. www.sei.cmu.edu/cbs/
23. Information Security Governance: Toward a
Framework for Action at www.bsa.org
24. Excellence in Security at www.pwc.com
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!



