Remote Video Auditing Creates Value

A service that seems to deliver on all these requirements, remote video auditing (RVA), is quickly gaining momentum in today’s marketplace. Managers are sent weekly e-mail scorecards that summarize an individual location’s performance. The reports contain pass/fail hyper links to video clips and still images, providing visual documentation of events uncovered by the auditing service. By utilizing RVA, companies can track events, breaches and business practices at customer locations.
RVA’s premise is both simple and revolutionary: leverage existing hardware and galvanize with enhanced software and services to produce increased return from current investments. The auditing system uses the Internet to leverage remote viewing through very inventive uses of video, to help businesses reap benefits from their recorded video.
Alone and unmonitored, recorded data is worthless. Audited and analyzed, however, the findings can produce a bevy of valuable information for businesses spanning retail, fast food, food processing, convenience stores and transportation.
According to Adam Aronson, CEO of New York City-based Arrowsight Inc., “Sending reports to make, save or reduce spending is becoming a must-have due to the need to reduce costs and drive productivity. RVA offers companies a threefold value proposition – increased return, reduced overhead and improved efficiency.” Aronson’s company, along with partner, Tyco subsidiary ADT Security Services, develops RVA software and services and delivers daily, weekly and monthly audits and compliance reports. The reports monitor compliance, reduced shrinkage and job performance and provide access to videos and still images.
Extrapolating from his pioneering work in childcare remote video viewing services with former company ParentWatch, Aronson looked to how the technology could be applied to other industries. He logged hundreds of hours monitoring convenience stores, fast food chains, retail stores and food processing plants in order to identify the common denominators of business. He also observed recorded video could have many uses beyond security, including compliance, productivity, customer service and cost containment.
The heart and soul of a security system is the camera and recording device. RVA software must integrate with existing hardware such as digital video recorders and data sources, encompassing point-of-sale, security systems and other enterprise data.
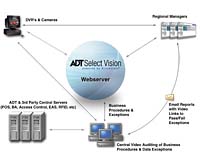
their operations and staff performance.
Every second counts
In a mobile economy, time is money. Few companies have become more familiar with this than the fast food industry, where the drive-through window represents a franchise’s cash cow. According to fast food giant McDonalds, the critical success factor is “time-in-line,” which specifically refers to the time it takes customers to get from the cash-pay window to the food pickup window. “The difference between 100 and 150 seconds is the death knell to drive thru operations,” notes Aronson. “Customers are at the fast food restaurant because it’s quick and they’re in the drive-through lane because it’s quicker.” RVA Services have dramatically improved time-in-line by integrating with the security cameras at the cash pay and pick-up windows and monitoring movement.Tony Delligatti, owner of three McDonald’s franchises in North Carolina, began using the video audit services at his locations to effect dramatic improvements, including increased sales by leveraging Arrowsight pass/fail score cards.
Delligati adds, “When we receive the audit report and are able to show our managers actual video of a car sitting at a drive thru for two minutes, it’s very powerful. It takes away excuses.” In addition to decreasing the time between paying and reception of a food order, Delligati uses RVA services to reduce food waste, increase employee productivity and ensure food safety compliance.
Compliance is critical
Nowhere is it more important to follow rules and regulations than in food processing, where the health and welfare of the public is at stake.For retail businesses, shrinkage is a growing problem that annually costs the industry billions of dollars. Arrowsight worked with Finish Line, a 500-store retail chain, at one of their target stores in order to implement a system ensuring compliance with basic security procedures designed to reduce theft, especially internal theft.
By giving the staff the perception that the premises were being monitored and audited at an off-site facility, Finish Line witnessed an astounding 63 percent reduction in shrinkage over a four-month period.
Security however, is not the only area that companies are interested in monitoring. RVA services also represent a cost-efficient method of culling marketing research. In an effort to improve research and development and increase sales, Pfizer retained Arrowsight to monitor the customer movement, behavior and overall viability of their in-store product displays at a major drug store chain.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







