Email security best practices for a remote human perimeter

We will soon be approaching one year since home and office coalesced into one nebulous mass for millions of people. Many organizations made temporary policy tweaks to adapt to stay-at-home orders in the wake of the coronavirus pandemic, but they are increasingly realizing that the future of work will include a permanently altered - and often remote - workforce. People are the most precious assets organizations possess, and they are also the assets most vulnerable to attack by cybercriminals. While the world around us has changed beyond recognition, the battleground for these targeted attacks remains worryingly familiar: email.
Cybercriminals quickly weaved the pandemic into their email scams earlier this year, and more recently impersonated the IRS by pretending to share updates about COVID tax relief in an attempt to steal sensitive tax information. In mid-April, Google’s Threat Analysis Group reported that they detected 18 million COVID-19 themed malware and phishing emails per day. And that’s without including all the email impersonation, invoice fraud, and phishing attacks that have nothing to do with COVID, but are dangerous nonetheless.
In this article, I will provide some tips to help individuals and organizations communicate more securely over email.
Tips for employees
1. Look out for social engineering cues in emails
When you read an email that’s meant to make you think fast, try to think slow. Targeted email attacks are often crafted with language that induces a sense of urgency or fear in victims, coercing them into taking the action the email wants them to take. Not every email that makes us feel these emotions will be a scam, of course, but it’s an important factor to keep an eye out for nonetheless.
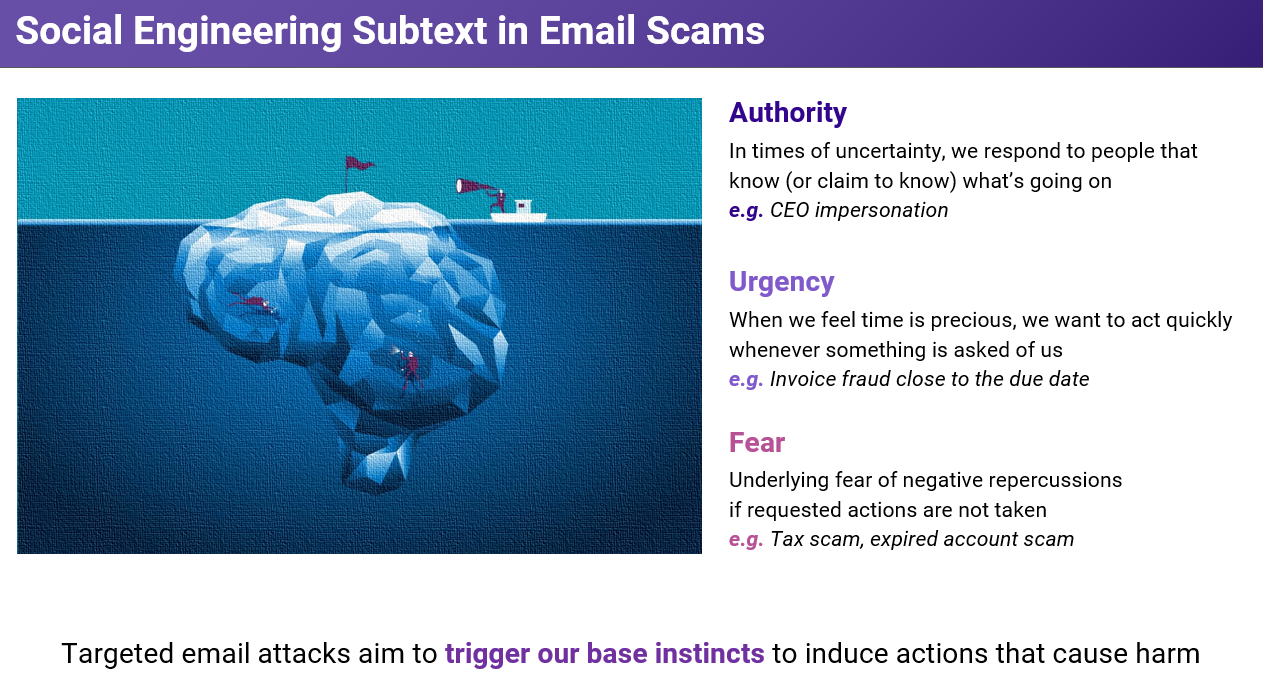
Here are some common phrases and situations you should look out for:
- Deadlines given at short notice for processes involving the transfer of money or sensitive information.
- Unusual purchase requests (e.g. iTunes gift cards).
- For payroll teams: employees requesting sudden changes to direct deposit information.
- For partner/finance teams: vendor sharing updated bank account details at short notice, usually right before an invoice is due.
2. Use 2FA on your accounts - and your workflows
If you haven’t already, it’s definitely a good idea to enable two-factor authentication (2FA) on your business and personal accounts. Having 2FA on just your business accounts doesn’t solve the entire problem, because cybercriminals can still compromise your personal account and impersonate you in emails to your employer or family.
You should try to replicate 2FA, even if in a loose sense, for any email that makes unusual requests related to money or data. For example, has a vendor emailed you with a sudden change in their bank account details, right when an invoice is due? Call or text the vendor and confirm that they sent the email. Even if the vendor is very busy, they will understand and appreciate your caution.
3. Don’t get too comfortable with automated emails from brands
You probably get tons of emails from your favorite online marketplace, streaming service, email provider, and other consumer brands every day. You probably click those emails and perform the requested actions (update password, provide shipping address) without thinking twice. Cybercriminals know this, and often impersonate these brands in emails and try to steal sensitive data.
Many of these attacks have a lot of thought put into them to make the workflow seem legitimate. Whether it’s a message from a bank asking for your security challenge questions, or a working CAPTCHA to lull victims into a false sense of security, no seemingly mundane email is safe from potential exploitation.
Even when you’re very busy, try performing a context check on an email before following through on its requested action. Will your phone company really ask for your SSN over email? Will a streaming provider send an email to your business address even though your account is linked to your personal address? Spending a few seconds here can save a lot of strife down the line.
Tips for security teams
1. Bring your security awareness program closer to reality
Security and phishing awareness programs have certainly made a positive impact on organizations’ preparedness against phishing attacks. However, they can oversensitize end users to report emails en masse to the organization’s phishing mailbox, thus overloading the security team. End users also usually don’t get any feedback when they report an email, remaining unaware whether the decision they made was the right one.
To complement security awareness programs, you should consider educating end users when real-life suspicious emails hit their inbox. In-context education like explanatory email warning banners can sensitize users with relevant examples from their inbox. These banners can include buttons for end users to mark the emails as safe or suspicious, thus taking some load off the security team.
2. Use organizational context to your advantage
Adversaries are not going to send mass phishing emails your way. The emails are more likely to come from someone you trust, like your manager, a trusted vendor, or a known brand. The emails will also include just enough context to make victims feel like it’s legitimate communication. Since adversaries are weaponizing your organization’s context to launch attacks, it stands to reason that you should also leverage this context in your email security stack.
Ensure that your security solutions measure communication baselines for your organization and users, enabling them to spot anomalies and catch targeted attacks that would otherwise slip past one-shot detection methods. Did a vendor just send an email with an urgent invoice to someone they don’t usually email? Is one of your employees suddenly forwarding tons of emails to their personal account after logging in from an unusual location? When email attacks lack traditional payloads, understanding and learning from organizational context is vital.
3. Don’t rely solely on native email security
A remote human perimeter has accelerated the adoption of cloud email by organizations, enabling them to simplify email delivery and reduce reliance on Secure Email Gateways (SEG). By 2023, Gartner predicts 40% of orgs will rely on native email security from cloud email providers as their first line of defense. Office 365 and G Suite have improved their native email offerings in recent years, providing good anti-spam and anti-malware protection. However, native security from cloud email providers should form the base - and not the entirety - of your email security stack.
Conduct a thorough audit of your native email security capabilities to find out (and deploy) what you have already paid for. Microsoft recently launched Office 365 Configuration Analyzer service free of charge, which will recommend the right configurations for native O365 email security policies, helping overriding rules and policies that give organizations lower protection. Once you’re clear what your native email security can and cannot do, make a plan for augmenting these built-in capabilities with security layers that are purpose-built to stop targeted email scams.
Securing your human perimeter may turn into a journey with a murky destination. Nothing you do will prevent 100% of email scams, but the intent is not to achieve a mythical level of protection anyway. The idea is to raise the bar for adversaries, making it as tough as possible for them to achieve their objectives of compromise. The tips provided above should help you start asking the right questions and get the building blocks of email security hygiene in place.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!








