Openness Opens Doors with IT and Physical Security
|
|
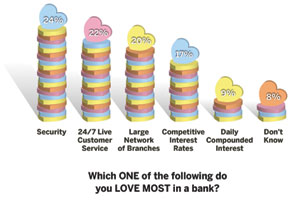
How do Americans love their bank? Security and round-the-clock customer service top the list. Bank security is one of those collaborative missions that bring together IT and physical security. According to a survey conducted for Ally Bank, 24 percent of respondents rank security as the option they love the most in a bank, followed by 22 percent who love 24/7 live customer service most. |
Warning: This article does not contain talk of convergence, silos, fusion, tipping points, disruptive technologies, a place at the table and all the other new-age, highfalutin mumbo-jumbo that too often says more about the speaker than the concerns of the listener.
You see, many enterprise security leaders have already gone beyond the “let me scare you management-speak” and moved on, successfully, to technologies and advances coming from physical security or IT or shared by both and in which the bottom line is the bottom line. No doubt, there are challenges with budgets, IT standards, sharing or accommodating infrastructure, among others.
However, when it comes to IT and physical security management, today’s business buzz is more soft spoken: collaboration, trust, situational awareness, understanding, data mining, interoperability, compliance and openness, all wrapped inside – to varying degrees at various times – the business mission. Before things get too Kumbaya, there are and will be bumps along the road. Still, security’s job must be done. And it is easier done, thanks to IT’s involvement and sometimes thanks to the bridging charms of savvy integrators.
At the Port of Wilmington in Delaware and operated by the Diamond State Port Corp. (DSPC), physical security had to go farther, a lot farther, than a typical electronic card access control system with implementation of the Transportation Worker Identification Card or TWIC. Welcome to the world of identity access management. IAM covers people, processes, facilities, and products to identify and manage the data, to authenticate users and grant or deny access rights to property, data or system resources. The goal of IAM is to provide appropriate access to enterprise resources.
Open to Diverse Technologies
At the port, by using special software, deployed on mobile readers as well as a desktop computer system, port officials are able to register TWIC holders and transmit that information to the existing card access system. The cards can then be read at fixed card readers located at various entrances and access points throughout the port.
TWIC credentials are required for entry to the port by anyone requiring frequent, unescorted access to the facility, entirely designated as a secure and restricted area. These include longshoremen, truck drivers, surveyors, agents, chandlers, port chaplains and laborers who access secure areas. Tenants who have their offices at the port, such as produce giants Chiquita and Dole, are also required to be enrolled in TWIC, which adds a layer of security at ports by ensuring that workers in secure areas have received a background check and do not pose a national security threat.
The special software enables the port to access the Transportation Security Administration’s real-time databases to better and faster determine if a credential has been revoked.
Enrollment, training and management of the program are handled by Jerry Custis, DSPC security manager, and Matthew Eskridge, DSPC security supervisor. In a unique outreach enrollment project, “mobile readers were taken to local union halls to enroll longshoremen,” says Patrick Hemphill, recently retired manager, port security and facility security officer. “This saved a lot of time,” he explains. By the way, the port’s human resources executive first spotted the special software at a conference demo. And Eric Schaeffer of Advantech Inc., the port’s systems integrator, aided in testing the project before its implementation.
Collaboration, trust, interoperability and compliance all came together to make business at the Port of Wilmington more secure and efficient.
Other integrators also see the change. Bruce Sachetti, director of IT for ADT Commercial and who has worked the field for more than a quarter century, has seen differences as computer and communications factors impact physical security overall. “Physical security and IT are best involved together from the start. It helps in complex project management.” He warns, though, that “common transport does not mean interoperability. The emergence of standards, many coming from IT and Internet Protocol (IP) developments, is making a big difference.”
“Today it is a good thing for end users to leverage their integrator,” adds Sachetti.
And that leverage includes project management, points out Ryan Pipes, security engineer at C&S Companies, a full-service, project delivery specialist and consultant firm. With emphasis on business solutions, Pipes points out a common goal should be seamless building, protecting, enhancing, and maintaining of the enterprise’s valuable assets.

|
|
By 2015, it’s estimated that there will be one trillion connected devices on the smarter planet. While many of these intelligent and instrumented endpoints are providing great opportunities, they are also creating emerging security vulnerabilities that enterprises and their physical security and IT executives need to address. |
It’s a Matter of Infrastructure
“Infrastructure is often the key to any project. And the existing network is often not able to handle everything,” says Pipes. “It’s helpful for security and IT to understand their own and each other’s roles” within the context of the business. “There also is the matter of ownership” of the infrastructure. The security engineer advises that collaboration could result in financial backing from IT for certain types of physical security projects. “And then there is the assistance through service and maintenance, too. All these worlds are coming together.”
Faster, more accurate situational awareness is another tool best achieved through partnerships that can include security, IT, an integrator and technology providers.
Take, as one example, a unique management solution for Bergen County, N.J.’s Department of Human Services (DHS). Through integrator New Jersey Business Systems, which specializes in networking, communications and computer services, a new system provides more accurate identification of homeless individuals who are seeking and receiving services from the county and feed more detailed data to the larger New Jersey state database, a repository of homeless population information that helps to serve the community through food, clothing and housing programs. Bergen County DHS required a solution that would take advantage of the existing New Jersey Homeless Management Information System while providing more accurate reporting about the true number of individuals for whom the county was providing services.
“User friendliness was one of our primary goals and we have that in this system,” says Valerie Dargan, director of the county’s DHS. “We open a Web page, select the service and location, apply the finger image, and we’re ready to go.” Although the new biometric system for Bergen County is currently based on finger scans, it has the option to become multi-biometric. A series of Web-based controls and Web services allow expansion and adaption as system requirements change and provides secure, rapid deployment of Web-enabled solutions.
Such “in the cloud” solutions are at the heart of yet another means of collaboration and compliance of physical security and IT.
Security is now a much broader ecosystem, says Mike Bliss, manager of channel marketing for security at Honeywell. He believes there is need for greater interoperability, not only among access, security video, fire, and intrusion, but expanding outward into building management and asset protection. There is added value of physical security systems to do more and be smarter, adds Honeywell colleague Beth Thomas, responsible for integration of systems and controls between IT and physical security. Especially for new buildings, there are now energy management needs, she adds.
That all means more collaboration among security, IT and the integrator, says Bliss. With the need for security to cover more doors, thanks in part to IP and less expensive door controls, designs will call for managed – in the cloud – solutions and linkage of security databases into IT’s Active Directory or an equivalent.
The Active Directory Model
Active Directory (AD) is a directory service created by Microsoft. It uses a number of standardized protocols to provide a variety of networked services and creates compatibility with many management and query applications. Active Directory stores all information and settings for a deployment in a central database and allows administrators – whether physical security or IT – to assign policies, deploy, and update software.
Among “working together” ideas from Thomas: Security should help out with his or her expertise when viewing protection of data centers and IT equipment closets.
Yet another path to collaboration is emerging use of smart cards, such as those with multi-functionality at colleges, and in the form of personal identification verification or PIV cards in military, federal agency and government contractor applications, comments Bliss.
And soon to be elsewhere, maybe.
The PIV card is an ID card that contains a computer chip, which allows it to receive, store, recall, and send information in a secure method. The main function of the card is to encrypt or code data to strengthen the security of people, information and physical access to secured areas, while using a common technical and administrative process. The method used to achieve this is called Public Key Infrastructure (PKI) technology. It is an accepted global business standard for Internet security. As an added benefit, PKI can provide the functionality for digital signatures to ensure document authentication.
There is a push to expand PIV into enterprise use, beyond government and military. The standard provides an identity management framework that enterprises should regard as a best practice in the design and implementation of their own identity management programs, contends the Smart Card Alliance, the trade organization whose members surely will gain from such an expansion. In spite of the push for higher security, interoperability and decreased barriers to entry emerging, PIV cards are right now being adopted slowly outside the governmental use case, says Peter Boriskin of UTC Fire & Security. Still, with the growth of open systems and complementary growth of security technologies that go beyond security into businesses processes, Boriskin says to expect an “interesting emergence of nontraditional players” and applications.
Driving the Bus
Beyond such expectations, the need for more security across diverse business processes in enterprises is coming from the tech end, suggests Mark Jett, manager of engineering for integrator Protection 1. He adds that it’s just a matter of producing more business benefits” from collaborations and synergies among systems and information, he says. By continuing to move to a shared infrastructure, there is reduction in the cost of ownership of technology overall in the long term. There are also more standards in the manufacturing of physical security products, software, and systems as well as industry-driven IT standards, too.
While Jett believes that typical network infrastructure was not intended or perceived to carry security video, the hard-nut-to-crack of security video standards, interoperability, openness, networking and integration is being addressed by a number of industry-centric forums and alliances.
Coming slightly from different perspectives but surely seeing the same end-point, the Open Network Video Interface Forum (ONVIF) and the Physical Security Interoperability Alliance (PSIA) showed off their achievements at the March 2011 ISC West show in Las Vegas. Both organizations are primarily made up of equipment and software makers, with some members in both organizations.
Claiming more than 650 compliant products in early 2011, ONVIF has recently added video storage and analytics to its core specification focused on an open, global standard for the interface of network video products.
PSIA claims that several thousand industry professionals have accessed its existing specifications including the IP Media Device for IP camera and video management system (VMS) compatibility; the Recording and Content Management specification, which standardizes the way recording and content management products interface with other devices in the security ecosystem, specifically security management systems; the Video Analytics specification that enables video analytic platforms of all types and brands to automatically integrate with video management systems and physical security software; and the PSIA Common Metadata and Event Model. There is also an access control specification from PSIA. And ONVIF also is working on its own IP standards beyond video.
The full effects of such security video standards efforts are still to come; but the stars seem to be coming together.
Sophisticated Software Comes Customized
Some interoperability standards still do not reach sophisticated VMS and PSIM or physical security information management products. Often sitting on top of VMS, PSIM is a kind of a mashup of integration of security system information, analysis, policies and proactive actions. According to research firm Frost & Sullivan, PSIM is becoming fundamental for next generation fully integrated physical security systems to offer advanced functionalities and to present a clear return on investment.
“While PSIM is seeing a higher degree of customization coupled with increased connectivity, many participants believe that PSIM functionality can or should be created with off-shelf software and not by customization options,” notes Frost & Sullivan Research Manager Matia Grossi. “It is anticipated, that while the standardization process gains momentum, the need to provide customized solutions will remain dominant in the market.”
Still, software development and processor power have accelerated the adoption of PSIM. Today, the majority of the deployments is mainly at maritime and airports, with critical infrastructure, homeland security and law enforcement applications also installed.
Firms such as VidSys, Proximex, IPVideo and others continue to upgrade and expand their software. For example, Proximex, with event and information management for both physical and logical security, improved its offering late last year through communications outreach and collaboration activities between an organization’s security personnel and other employees and/or internal resources impacted by a security incident.
In many instances, physical security personnel must join with others inside the organization to bring awareness to and resolve incidents. For example, a power outage at corporate headquarters will probably impact facilities, building employees and local police in addition to the security team. Other employees in operations, IT and building management may require accurate and immediate information to facilities activities. The technology gives physical security teams the tools to quickly circulate the right information from all integrated systems in order to keep parties informed and, as a result, resolve incidents faster.
Double Up With PSIM
At Con Edison, one of the nation’s largest investor-owned energy companies, there is an incident management platform for security operations which also streamlines safety and security procedures and improves compliance with the North American Electric Reliability Council’s Regulations on Protecting Critical Infrastructure. Information from video, security sensors and other management systems combine to form a common operating picture.
Chalk one up to integration.
But what about trust?
Just ask Stephen Hanna, co-chair of the Trusted Network Connect (TNC) group, who is also a Distinguished Engineer with Juniper Networks. “There are plenty advantages to use of Internet protocols and they have reduced cost while streaming access and video over networks. But it comes with some risks,” Hanna says. TNC is an open architecture for network access control, promulgated by the Trusted Network Connect Work Group of the Trusted Computing Group.
He sees a lot of collaboration including “back-in integration where physical security shares its data with logical. When someone is in a building, that information is shared with network access control for better local awareness.”
On the access side, Hirsch Electronics, a supplier of physical access control and security management solutions, is a member of the Trusted Computing Group and participates in its TNC work group to enable more secure computing across the enterprise. With other member companies such as IBM, HP, Microsoft, Juniper, Intel and RSA, Hirsch is part of an effort to drive open and secure networking capabilities into physical security industry products.
When it comes to IT and physical security management, Steve Vinsik, vice president, Critical Infrastructure Protection for Unisys Federal Systems, has seen it all. “It is an exciting and explosive time. Technology and advantages are coming at us from all angles. Video opens up issues. But everyone is getting along better than ever.”
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






