Chrome gets patched again, but 83% of users aren’t running the latest version

According to Menlo Security, Google Chrome users don't always take time to relaunch browser updates, and some legacy applications don't support new versions of Chrome.
Menlo Labs discovered that there are 49 different versions of Chrome being used by their customers as of November 17. Nearly two-thirds (61 percent) are running the latest build (.86) while just over a quarter (28 percent) are running one version prior (.85). Out of the customers running .86, a staggering 83 percent are running versions of Chrome that are vulnerable (<Chrome/86.0.4240.198). If these customers were using legacy-based detection approaches, these active zero days would have been a risk for them, says Menlo Labs.
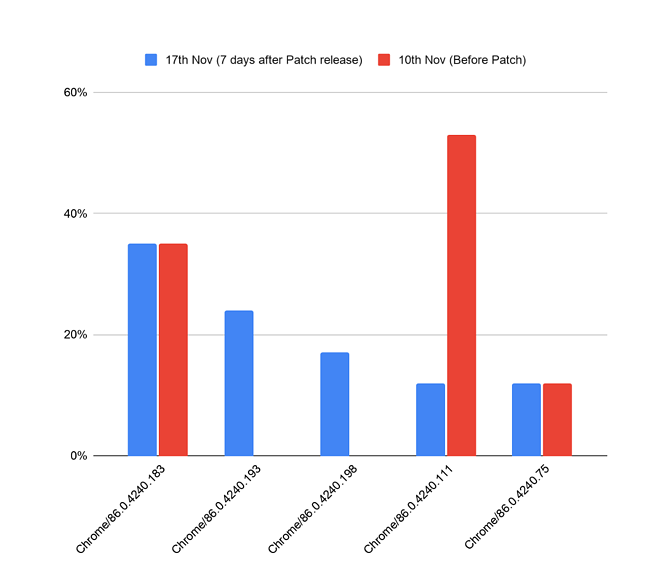
The chart below shows the top five versions of Chrome 86 seen on the Menlo platform as of November 17. The data shows that even though a patched version of the browser may be available for more than six days, customers are still not running these versions.
Tim Wade, Technical Director, CTO Team at Vectra, a San Jose, Calif.-based provider of technology which applies AI to detect and hunt for cyberattackers, explains that so long as there are zero days, which appears to be an indefinitely long, unceasing period of time, prevention will have a failure rate.
"Further, the current state of organizational overinvestment in prevention is almost always an exercise in expensive, marginal (if any) increase in capability rather than a transformative increase in capability – at the stifling cost of paralyzed business objectives and increasingly constrained productivity. What’s more important than prevention is resilience, which involves identifying security investments that minimize the impact of an attack. And yes – so long as adversaries can enjoy enormous economies of scale through Chrome – it’s nearly everywhere – it will continue to receive targeted attacks," says Wade.
Jack Mannino, CEO at nVisium, a Falls Church, Virginia-based application security provider, notes, that because web browsers interact with many different software packages on an operating system, it makes it impossible for a single product to protect web users from all conceivable attacks delivered through the browser.
Mannino adds, "Attackers will continue targeting web browsers because this remains a great entry point to compromising endpoints inside of an organization. Browsers are a great way to deliver exploits across a variety of technologies supported by browser extensions and plugins. Web browsers tend to be patched faster in many organizations than other applications and packages. Extensions tend to be updated less frequently, with less enterprise controls enforced for hardening these additional attack surfaces."
Hank Schless, Senior Manager, Security Solutions at Lookout, a San Francisco, Calif.-based provider of mobile security solutions, says, "Since the vulnerabilities are in the app itself, it requires more than just monitoring web traffic to prevent zero days. Mobile app vulnerabilities will always pose risk for organizations. In order to have an airtight security strategy, you need to know when vulnerable apps are present in your fleet as soon as they’re disclosed. Since it takes time for people to update their apps, attackers will continue to target the Chrome browser."
"These vulnerabilities are only patched if the user updates their app. Since many people don’t have automatic updates turned on, it’s likely attackers could still find success in exploiting these vulnerabilities. In the case of a successful exploit on mobile, the threat actor gains access to anything the Chrome app has access to. This includes browsing history, the camera and microphone, and location data. Malicious access to this data could put corporate data at risk if the user accesses any corporate resources through Chrome. Exfiltration of this type of data could also lead to compliance and other regulatory violations,"
Without visibility into the mobile apps on your employees’ mobile devices, it’s impossible to tell whether a vulnerable app could be threatening your corporate infrastructure, Schless adds. "Most everyone has a tool in place that does this for computer apps. With the amount of data access mobile devices have now, they should be treated with the same priority when it comes to your security strategy. Using a tool that can provide actionable information on mobile vulnerability and patch management is key to preventing a breach."
Zero Trust is also a big part of this, Schless explains. "You need to be able to extend policies to mobile devices that require them to have the most up-to-date version of apps in order to access corporate infrastructure. Executing this type of policy is a best practice of ensuring strong mobile risk and compliance management. "
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






