Eyes with Brains
According to Frost & Sullivan Senior Research Analyst Soumilya Banerjee, there’s also a shift in demand from digital to IP-based security systems that permits remote monitoring. Improvement in image quality and analysis is another focus area. The incorporation of algorithms has made it possible for security video systems to send out alerts before or during the initiation of a crime and ultimately assist concerned authorities in taking immediate action.
“It is expected that developments in chip technology will also eliminate undesirable interference in the images, resulting in far superior picture clarity,” explained Banerjee. “Cameras can be expected to be able to capture more number of pixels and also allow operators to zoom in on particular elements of interest while retaining high picture resolution.”
Another area of focus gaining popularity is video motion anomaly detection (VMAD) systems, which have a preloaded algorithm to help users study the movement of pixels within the image. These smart cameras can also identify objects that are partially or completely hidden from view for a certain period of time.
Cameras as weapons
There are more aggressive security camera designs in the light of terrorism and military needs.Some manufacturers are working on intelligent cameras with non-lethal weapons that have the ability to lock on their target, measure the distance and shoot if the target is within a range of 50 feet. These cameras are also expected to gain acceptance in extremely high security and high-risk areas such as prisons or covert government research facilities.
There are still smart camera challenges.
Although the acceptance of smart cameras is highly promising, manufacturers need to solve the issue surrounding the false alarm rate.
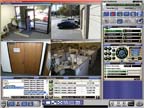
Systems integration also brings intelligence to security video. One example from Keri Systems of San Jose, Calif., is the Visions video platform, which combines the firm’s access control hardware and software with digital video technology. When integrated with access software, cameras are automatically configured to coincide with doors, gates or other input points. Subsequent QuickSearch reports will communicate with the Visions Server application to find and list any access system events that also have associated video clips, and play them back in a viewer window on demand. The server records and retrieves all video events, as well as providing on-screen camera control and live monitoring via a powerful, easy to use interface.

Embedded OS technology improves performance and reliability with enhanced logic implementation to continually tag video with the associated alarm events, even in an offline condition from the host.
There also is specific intelligence built into cameras. Honeywell of Syosset, N.Y., has a wide dynamic camera, a high-resolution body camera designed for environments with high contrast and changing light conditions. It uses patented technology to convert images from analog to digital format within each pixel immediately after the image is captured. Uniquely each pixel in the camera acts as its own camera having an independent shutter speed, optimizing the exposure time for every picture detail.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!




