Patches? We Don’t Need No Stinkin’ Patches!
Patches are boring.
Patching is boring.
Patching is tedious and time consuming.
Patching is also necessary.
At NTT Security, we continually observe hackers attempting to attack our customers’ networks using vulnerabilities. Approximately 75-80 percent of those vulnerabilities are three years old or younger. That means 20-30 percent of the vulnerabilities attackers are using at any given time are more than three years old. In fact, we regularly detect exploit attempts against vulnerabilities which are 3, 4, 5 or even 18 years old – the vast majority of which can be alleviated by applying patches.
Think about that for a second.
If you can patch all vulnerabilities in your environment that are more than three years old, you can eliminate 20-30 percent of all targeted vulnerabilities. Patching these vulnerabilities means cyber criminals can no longer exploit them to attack your environment. If you patch every vulnerability over a year old, you can remove as many as 75 percent of the vulnerabilities attackers are targeting right now. And even if you only patch the top 10 vulnerabilities, you can reduce up to approximately 80 percent of all cyber-attacks currently taking place before they pursue other points of entry.
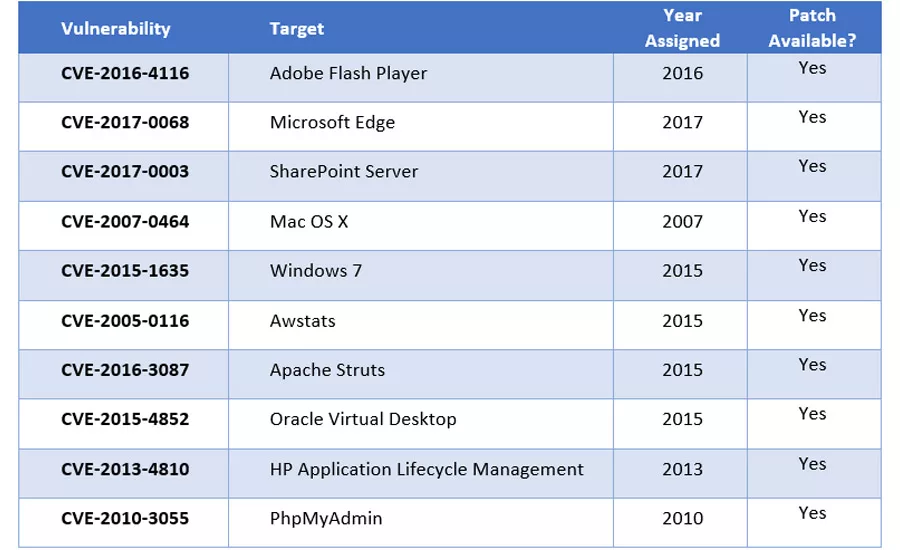
The above table includes some of the most common vulnerabilities attackers have been attempting to exploit against client environments so far in 2017.
These top 10 vulnerabilities accounted for over 88 percent of all exploit attempts during the first four and a half months of 2017. They all have patches available, and only three of them are less than a year old. If you can patch all 10 of these vulnerabilities, it can result in a dramatic reduction in the potential for exploitation.
If 10 vulnerabilities are too much, perhaps we should talk about just one specific example. The WannaCry ransomware making the circles recently takes advantage of a SMB vulnerability defined in MS17-010, which was being exploited for as much as three weeks by other attacks before we saw WannaCry. Just think about the amount of chaos and media coverage WannaCry has received since it hit on May 12th. If everyone had previously applied the MS17-010 patch, and virtually no one was vulnerable to the exploit, WannaCry would have been a “nonstory.”
One of the problems with setting expectations on patching requirements is that every organization is different. They have different environments, different tools, and different skill sets. What may be simple in one organization may very well be impractical in another based on the complexity of the organization’s patching priorities and policies. It may very well take only minutes to apply specific patches. If the lack of those patches exposes a company to a potentially catastrophic breach such as compromising millions of credit cards or health care records, then the time required to install the appropriate patches would have been well worth the time and effort. Worse yet, if an organization knows software patches have not been applied and takes no action to remedy the situation, they could be considered negligent and held liable, and suffer significant financial and public relations consequences.
Another common challenge is that IT and/or security personnel may not know of all the software employees have installed on their devices, and therefore are unaware they need to keep it current. Software obtained as “evaluation copy,” or worse, that is pirated, also falls into the “unknown” category as patches are probably not available or obtainable. These situations make networks inherently more vulnerable, and elevate the likelihood of a successful cyberattack.
Even if software patches are not a silver bullet which will prevent cyberattacks, they can surely prevent a significant number of them. And software patching should be a manageable process when policies are put in place to ensure they happen. If keeping our systems up to date with software patches can really reduce potential exposure to cyberattacks by as much as 80 percent, shouldn’t it be a priority for security and IT professionals?
On or before May 12th, if you had to choose between having your network held for ransom by WannaCry, or performing the boring task of installing a single patch from Microsoft to eliminate the problem, which path would you have taken? The answer is obvious.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!




