How to Sort through Big Data for Threat Detection

|
| Image courtesy of Ernst & Young. |
In the age of Big Data where volume, velocity and variety of data is increasing complexity both internally and externally, integrating new data sources is bringing organizations tremendous opportunities to mitigate threats in new, innovative ways.
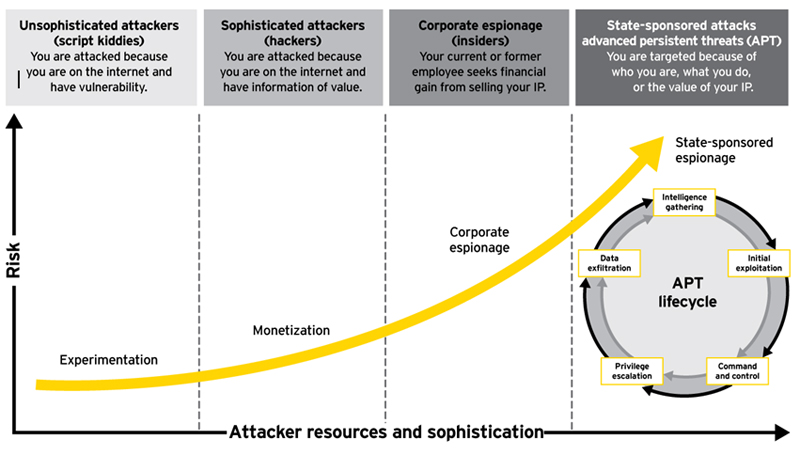
Scanning through news articles, there is a steady proliferation of headlines on fraud, corruption and espionage. Whether it’s a rogue trader in London, U.S. companies bribing government officials for permits in Latin America, or a foreign government’s cyber army pursuing target U.S. companies, great attention has been paid to developing sophisticated countermeasures. Companies now have forensic accountants and ex-hackers on payroll, and many governments have law enforcement and military divisions dedicated to fighting corruption and wars in cyber space.
Looking inward
It is easy to label corrupt governments and external hackers as the enemy. However, often coworkers that you trust and see every day can be the ones committing fraud, sabotage and espionage, from the inside. Internal controls have moved mountains since SOX (Sarbanes-Oxley), but as recent financial industry failures have proved, these can be defeated. Firewalls keep unwanted visitors out, but as WikiLeaks demonstrated, insiders regularly steal valuable sensitive information.
Numerous studies and recent history show these insider events are not isolated incidents. How can organizations proactively identify risk of insider incidents while maintaining the balance between vigilance and privacy?
Data Overload
Fortunately (and unfortunately), we live in an age surrounded by data that is growing exponentially. According to Gartner, only eight percent of information generated actually gets analyzed. We can now look at the thorny issue of insider threats proactively from a more behavioral perspective rather than dealing with the problem reactively(a.k.a. too late). This doesn’t mean blindly buying into the buzz around big data, but rather making sure that informed context and actionable insights can be developed from the intersection of data and analytics. With terms like petabytes, Hadoop and predictive modeling, this process can easily become overwhelming. The key is to be focused, keep the results simple, and never forget to ask “so what?”
Concealed constructs of insider events mean direct proofs are inevitably difficult to find. But that doesn’t mean insiders are immune to behavioral changes – physical and psychological – often associated with clandestine activities. Detecting these changes has long been a favorite tactic for the law enforcement and intelligence agencies.
Explosive growth in communications, sensor, social and other varieties of data that permeate the corporate world today offers a cost effective opportunity to monitor for these subtle and gradual behavioral changes as a significant risk factor to information assurance.
Focusing outside of the box
Take emails and instant messages. We can now apply advanced linguistic analysis with relative ease to identify changes in underlying emotive tones. One of the most famous case studies of this exercise is the mapping of emotive tones on emails by Enron executives at around the time of its infamous collapse. Starting in October 2000, the volume of “derogatory” and “confused” emails began to increase dramatically and spiked in October of 2001, coinciding with the timing of the financial scandal.
Sensor data, such as badge readers and biometric scanners, is another great source to look for changes in behaviors. In near real time, we can apply quantitative algorithms on billions of records to identify patterns that significantly differ (in a stochastic sense of that word) from normal. For example, abnormally concentrated badge swipes through a sensitive research facility right after the annual performance review may warrant closer scrutiny. That, when combined with an individual’s time reporting information, email communications or sales activity can now come together to paint a more complete risk profile.
Multiply the number of information sources (accounting, travel, social media, etc.) and increase the volume, and one can easily see this application of big data analytics forms a rational framework to detecting the risks of insider threats. In a hyper-connected global economy, fraud and espionageis not only lucrative, but can sometimes be a competitive practice, especially in emerging markets. Companies need to be mindful that such activities are not only driven from the outside, but often develop at home. By integrating relevant analytics on data already available, companies can build an effective defense against insider threats.
|
|
Image courtesy of Ernst & Young. |

|
|
Image courtesy of Ernst & Young. |
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







