Eye On Your Enterprise
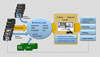
Physical security information management systems create a command and control platform across diverse sensors and components. Security sets up rules, workflows and scenarios to equip the operator with situational awareness and actionable information. Photo courtesy of Proximex
Say hello to a new buzz phrase. Don’t be afraid. This one’s all business, but comes with brains, brawn and a dash of cost savings after an initial investment.
Physical security information systems (PSIM) are in a new security technology class that combines diverse physical security sensors and devices and completely manages them from a single platform.
The concept is evolutionary.
What’s happening is that, as physical security infrastructures continue to grow, the need to manage these infrastructures becomes even greater and more complex. First view the traditional security environment: There are a host of security devices which include security video; analytics; storage such as network video recorders (NVRs) and digital video recorders (DVRs); electronic access control; intrusion alarm systems; fire alarm and life safety systems; building management systems; and other applications. There’s even a way in for the convergence with logical security.

Video is at the heart of PSIM but also a tricky application to integrate in.
BEYOND INTEGRATING AND INTERFACING
For most enterprise operations, each of these systems often operates within its own environment or they are interfaced in sometimes costly ways.The challenge with these systems is that they don't have an interoperating awareness of each other. The result is multiple physical security technologies working independent of one another which creates security management inefficiency.
Reviewing the history book of buzz words, it would be easy to jump to the conclusion that it’s systems integration. But PSIM goes way beyond that.
Tim Holloway, vice president technology, security solutions at Anixter, evaluates and selects technology and interoperability. “PSIM is a key for end-users. They can get more value out of the systems they are deploying. The bottom line is the ability to integrate systems together while presenting the information all together,” he said. “It’s still fairly new. And capabilities – compared to some expectations – are somewhat limited.” But, according to Holloway, the concept is true. You can configure a platform across multiple systems, present actionable information, provide scenarios and keep a record of the actions and reactions.
One of the most important elements of PSIM: the scenarios, workflows and rules that allow the system to “understand” what really is happening – situational awareness – and what to do – actionable information.
On the backside, observed Holloway, PSIM solutions need to be fed upfront and “programmed by someone who has thought through the scenarios. It takes diligence and accuracy. This isn’t plug-and-play. Be careful. You want to achieve systems and responses as completely integrated as possible.”
For many security leaders hopping on the PSIM bandwagon, they often share high-end solutions implemented for homeland security, critical infrastructure such as large power plants, ports and transportation centers, as well as other highly secure, labor-intensive organizations.

Ed Merkle, director of port security and emergency operations at the Virginia Port Authority, used a PSIM module to handle visitor access.
METRICS AND ROI
When approaching the issue of return on investment, it is important to view PSIM as a solution buy, not a product buy. PSIM also demands an understanding of the enterprise, its threats and responses in ways that go beyond cameras, readers, sensors and alarm monitoring. What the concept delivers is a platform that addresses specific “pain points,” that will differ in each organization. Eliminating those pain points brings reductions in cost that are all part of PSIM’s return on investment. For example, one pain point may be security’s cost of training operators, who – when they join their organizations – must learn to navigate existing and disparate systems. A PSIM platform providing a common operating picture with icons of cameras, fire detection, specialized sensors, access control and tracking devices eliminates the need to learn all of those systems.In addition, a PSIM platform that incorporates preprogrammed response actions to incidents such as hazardous chemical spills addresses another pain point, the need to have individual operators, security leaders and on-site first responders memorize a variety of differing responses.
Another example of an organization’s pain point could be a high number of false alarms, and the costs associated with responding to them. PSIM systems can prioritize an event such as a door being forced open during a period when detectors indicate activity in the building during non-working hours. By being able to prioritize these events, the severity level of the event can be ascertained and money can be saved on avoiding false alarms. For high security environments where a first responder needs to respond to every alarm, then there’s a cost that can be quantified and factored into the ROI equation.
For subsystem upgrades and moving from legacy technology, a PSIM platform avoids more expensive “rip-and-replace” situations.
UNDERSTANDING HIDDEN COSTS
Within the ROI equation, sometimes hidden is the operating costs of disparate systems and operations that might tie together more efficiently through a PSIM solution.
When considering PSIM, consider:
When considering PSIM, consider:
- A global understanding of your physical security infrastructure.
- Analyze how disparate or fragmented the infrastructure is, in terms of the number of DVRs, biometric devices, security video cameras, intrusion sensors, card readers, etc.
- Examine the compliance challenges the enterprise faces in attempting to comply with regulations from Homeland Security, the FDA, DEA, HIPPA and Sarbanes-Oxley.
- Analyze logical access management and physical access management to determine whether or not they operate in a similar manner. The goal is to streamline operating costs and risk management.
Another firm specializing in the PSIM sector – Proximex – recently upgraded its technology to address the visibility and decision-making requirements of security directors while streamlining management and integration processes for administrators.
"Security directors have the weighty responsibility to be aware of every incident that occurs and direct others to act properly on the 'right' events according to company policy," said Jack Smith, chief executive officer for Proximex. "It can be a huge undertaking to respond in the right fashion to the right incidents if all alarms are given the same importance within the security system,” he pointed out.
"Security directors have the weighty responsibility to be aware of every incident that occurs and direct others to act properly on the 'right' events according to company policy," said Jack Smith, chief executive officer for Proximex. "It can be a huge undertaking to respond in the right fashion to the right incidents if all alarms are given the same importance within the security system,” he pointed out.
AFTER-FACT ANALYSIS FOR METRICS USE
For security leaders, such technology includes summary views of incidents and new trend reports for better analysis of the security environment.
Smith appreciates the pioneering effort of PSIM sources. “There are many different vendors with different levels of the ability to interoperate.” He sees one key – reusable code for various flowchart designs and workflows. “There should be no limit.”
Empowering end-users through PSIM is a thought also shared by Andrew Wartell, a high level security consultant, who spent the last four years as vice president of global security and director of special projects at Goldman Sachs.
He pointed out that “security systems have become more complicated and capable. But often in the command center there still are ‘stovepipe’ systems. The large security systems providers haven’t really integrated them. The industry is getting there but slowly.”
What’s needed is “situation control and situation action. That brings all of these disparate technologies together and facilitates the ability to act quickly and learn from the experience,” said Wartell. PSIM as a common operating environment is a force multiplier. A next step: convergence of IT and physical but much more than now, according to Wartell.
Dave Fowler of VidSys mirrors Wartell and a focus on overcoming challenges.
“There needs to be establishment of standards as security unplugs existing stuff and plugs in new stuff,” he pointed out. I want an easy way to take what we see – risk assessment and/or policies – and put into the system.”
Smith appreciates the pioneering effort of PSIM sources. “There are many different vendors with different levels of the ability to interoperate.” He sees one key – reusable code for various flowchart designs and workflows. “There should be no limit.”
Empowering end-users through PSIM is a thought also shared by Andrew Wartell, a high level security consultant, who spent the last four years as vice president of global security and director of special projects at Goldman Sachs.
He pointed out that “security systems have become more complicated and capable. But often in the command center there still are ‘stovepipe’ systems. The large security systems providers haven’t really integrated them. The industry is getting there but slowly.”
What’s needed is “situation control and situation action. That brings all of these disparate technologies together and facilitates the ability to act quickly and learn from the experience,” said Wartell. PSIM as a common operating environment is a force multiplier. A next step: convergence of IT and physical but much more than now, according to Wartell.
Dave Fowler of VidSys mirrors Wartell and a focus on overcoming challenges.
“There needs to be establishment of standards as security unplugs existing stuff and plugs in new stuff,” he pointed out. I want an easy way to take what we see – risk assessment and/or policies – and put into the system.”
CONVERGENCE AS A PATHWAY
As Fowler sees it, “It’s a matter of how PSIM manages and enforces corporate policies through rule engines and workflows. Identity management is a way to bring things together for IT and physical security. It’s one risk management system for both. In addition, the concept also energizes business optimization.”
Fowler’s VidSys just opened a Virginia-based multi-vendor Convergence Center of Excellence with a PSIM focus. Built to showcase physical and logical security convergence and the industry expertise, experience, and technology in some of the largest command centers in North America, the facility promotes multi-vendor cooperation, industry standards and best practices from over 30 companies and organizations.
Chicago-based System Development Integration (SDI), which put in video and access control for a category X hub airport, installed a PSIM solution at the Windy City’s major exposition center and designed all technology for a state emergency operations center. “We’ve never had a client say, ‘Where is my dollar return?’” said senior consultant Tom Condon. “It’s all about a cost-benefit analysis.”
Condon’s colleague, Ray Erdman said that PSIM “is all so new.” Added Condon, “For large facility, the plan may be for everything to be connected. But should everything really be connected? This is a complicated process.” Erdman suggests that evolution to PSIM could be better done in manageable chucks.
Condon sees the brains and brawn of the concept by suggesting that workflows and scenarios drill down to a process of taking what’s in a security executive’s head and bringing it into the system. The key is accuracy. “Preparation beforehand is essential; support some sort of spatial component for accurate floor plans. See the doors; the cameras. The aim is the ability to audit an event and improve on the response in the future,” he said.
Of course, purely financial returns are most identifiable in the area of labor reduction resulting from the ability to do more with fewer people. That even makes sense when it comes to homeland security applications from airports and cities to ports.
Fowler’s VidSys just opened a Virginia-based multi-vendor Convergence Center of Excellence with a PSIM focus. Built to showcase physical and logical security convergence and the industry expertise, experience, and technology in some of the largest command centers in North America, the facility promotes multi-vendor cooperation, industry standards and best practices from over 30 companies and organizations.
Chicago-based System Development Integration (SDI), which put in video and access control for a category X hub airport, installed a PSIM solution at the Windy City’s major exposition center and designed all technology for a state emergency operations center. “We’ve never had a client say, ‘Where is my dollar return?’” said senior consultant Tom Condon. “It’s all about a cost-benefit analysis.”
Condon’s colleague, Ray Erdman said that PSIM “is all so new.” Added Condon, “For large facility, the plan may be for everything to be connected. But should everything really be connected? This is a complicated process.” Erdman suggests that evolution to PSIM could be better done in manageable chucks.
Condon sees the brains and brawn of the concept by suggesting that workflows and scenarios drill down to a process of taking what’s in a security executive’s head and bringing it into the system. The key is accuracy. “Preparation beforehand is essential; support some sort of spatial component for accurate floor plans. See the doors; the cameras. The aim is the ability to audit an event and improve on the response in the future,” he said.
Of course, purely financial returns are most identifiable in the area of labor reduction resulting from the ability to do more with fewer people. That even makes sense when it comes to homeland security applications from airports and cities to ports.
BRINGING TOGETHER AGENCIES ACROSS CITIES
Rob Henry of the City of Davenport has followed the evolution of physical security information management throughout its recent development.
“A few years back, we brought in Raytheon for a region-wide project which included a wireless network, collaboration among agencies while integrating a lot of different technologies. VidSys was brought in and funds earmarked for security video. But we had all different cameras, different software.”
So the real issue turned into the need for the community to have a total system with all the components possessing interoperability – voice, data and images.
But the ability of the project to go wherever needed came down to PSIM and its concept of working smarter across law enforcement, security, communications and IT. “It’s a question of situational awareness,” said Henry. “We need accurate and fast information and the amount of that type of information is critical.”
Henry added, “We want cameras in our neighborhoods. We have the backbone and with the VidSys technology, we can do that.”
“A few years back, we brought in Raytheon for a region-wide project which included a wireless network, collaboration among agencies while integrating a lot of different technologies. VidSys was brought in and funds earmarked for security video. But we had all different cameras, different software.”
So the real issue turned into the need for the community to have a total system with all the components possessing interoperability – voice, data and images.
But the ability of the project to go wherever needed came down to PSIM and its concept of working smarter across law enforcement, security, communications and IT. “It’s a question of situational awareness,” said Henry. “We need accurate and fast information and the amount of that type of information is critical.”
Henry added, “We want cameras in our neighborhoods. We have the backbone and with the VidSys technology, we can do that.”
IMPROVING PORT COMMAND CENTER OPERATIONS
For instance, the Port Metro Vancouver (aka Vancouver Fraser Port Authority) has a comprehensive, integrated security system to monitor, control, and ensure safe, secure, and efficient vehicular access to the port's terminals and facilities. Each of the control zones includes security and surveillance equipment, traffic control systems, dynamic electronic signing, and what the port calls immediate consequence devices. ICx Technologies’ software, in the centralized command and control center, monitors and controls all devices and systems, including over 100 video cameras, through a single consolidated user interface.
The port directly monitors security for two cruise ship terminals, two major waterways, and a seven km perimeter. This roadway is owned by the port and provides access to a number of key waterfront businesses. The project effectively overlaid significant security infrastructure on top of a high volume transportation route and directly resulted in the drastic reduction of unauthorized vehicle traffic. This not only significantly improved security, but also significantly increased the useable capacity of the roadway that serves as a vital commercial transportation link.
The command center is a highly functional always manned facility that monitors all assets using information from diverse systems. The high level of data integration allows operators to have situational awareness, actionable information and a more complete audit trail.
Among key components:
The port directly monitors security for two cruise ship terminals, two major waterways, and a seven km perimeter. This roadway is owned by the port and provides access to a number of key waterfront businesses. The project effectively overlaid significant security infrastructure on top of a high volume transportation route and directly resulted in the drastic reduction of unauthorized vehicle traffic. This not only significantly improved security, but also significantly increased the useable capacity of the roadway that serves as a vital commercial transportation link.
The command center is a highly functional always manned facility that monitors all assets using information from diverse systems. The high level of data integration allows operators to have situational awareness, actionable information and a more complete audit trail.
Among key components:
- High capacity physically and logically redundant LAN architecture
- Extensive security video deployment including IP, thermal and recording
- Traffic control devices (signal heads, digital signs, etc)
- Immediate consequence devices (tire shredders)
- Access control system
- Full fence intrusion detection system
- License plate recognition at all vehicle access points
- Biometric scanners
With so many components, the ability to bring useful information into the port’s command center is the essential bottom line.
ALTERNATIVES AND APPLICATIONS
As with any emerging technology, there are offshoots and hybrids.
Some approaches deal exclusively with video-enabled situation awareness.
Companies such as Cernium offer behavior packs to squeeze actionable information from video data.
Mount Holyoke College, for example, uses Perceptrak advanced video analytics software, integrated with Milestone IP video management software, to enhance the security of its South Hadley, Massachusetts campus.
The design analyzes video from security cameras for events of interest and adds metadata about the content, enabling enterprises to monitor, manage, distribute, store and query video. Security operators are alerted in real-time only to situations that require attention, and a database of events simplifies searches for critical video information during investigations.
"It provides our campus community with an additional layer of security," said Doug Vanderpoel, director, auxiliary services at Mount Holyoke College. "The intelligent video technology immediately alerts security personnel to suspicious activity, allowing for a more proactive response to potential incidents."
Vanderpoel added that the technology “gives us the opportunity to expand our cameras inside and outside.”
Some approaches deal exclusively with video-enabled situation awareness.
Companies such as Cernium offer behavior packs to squeeze actionable information from video data.
Mount Holyoke College, for example, uses Perceptrak advanced video analytics software, integrated with Milestone IP video management software, to enhance the security of its South Hadley, Massachusetts campus.
The design analyzes video from security cameras for events of interest and adds metadata about the content, enabling enterprises to monitor, manage, distribute, store and query video. Security operators are alerted in real-time only to situations that require attention, and a database of events simplifies searches for critical video information during investigations.
"It provides our campus community with an additional layer of security," said Doug Vanderpoel, director, auxiliary services at Mount Holyoke College. "The intelligent video technology immediately alerts security personnel to suspicious activity, allowing for a more proactive response to potential incidents."
Vanderpoel added that the technology “gives us the opportunity to expand our cameras inside and outside.”
EMBEDDING FEDERAL REQUIREMENTS
Another hybrid of the PSIM concept is embedded in the Virginia Port Authority’s Trusted Agent program that employs a unique tracking solution from Orsus that is part that firm’s Situator. The technology monitors visitors if they do not have a Transportation Worker Identification Credential (TWIC).
The port provides these visitors with a Nextel Sprint phone equipped with a radio and navigational system. When paired up with Situator, it provides command center operators the ability to track and monitor their whereabouts on property and directly contact them.
TWIC requires that anyone needing access to secure areas of Marine Transportation Security Act-regulated vessels and facilities to have a Coast Guard issued identification credential or be escorted at all times.
According to Ed Merkle, director of port security and emergency operations, some people are one time visitors, such as truckers who have been trusted with bringing secure cargo across the country but do not have a TWIC card. The other challenge is when a TWIC card carrying person forgets his card for the day. These people would then need to be personally escorted to gain access to the port.
Trusted Agent will enable the authority to maintain TWIC compliance. The handheld device can notify dispatchers by communicating via Situator if the visitor with the device enters a restricted area, a section of the port he is not authorized to enter or if the device doesn't move for a pre-defined period of time. Such situational management tools are also “a good blend between physical and logical security,” added Merkle.
It also comes down to workflow, rules from the end-user so that the system has the ability to say what to do. And one byproduct of such an approach is the ability to hone routines and reprogram appropriate responses. Added Merkle, “On the fly, I wrote a set of instructions inside Situator for mass notification.”
Again, such tools provide both situational awareness and actionable information that matches the security mission with the business mission.
Major government systems integrators are catching the PSIM bug.
The City of Boston, for example, deployed enhanced situational awareness during April’s Boston Marathon.
Raytheon Integrated Defense Systems operationally deployed a system to integrate existing video, mapping, location, tracking and operational information into one common operating picture. Aimed at public safety and emergency management, Roderick Fraser, City of Boston fire commissioner, said, "This project demonstrated that we have the capacity to integrate current systems to provide better situational awareness in a geospatial way for all public safety agencies that we haven't had in the past."
The port provides these visitors with a Nextel Sprint phone equipped with a radio and navigational system. When paired up with Situator, it provides command center operators the ability to track and monitor their whereabouts on property and directly contact them.
TWIC requires that anyone needing access to secure areas of Marine Transportation Security Act-regulated vessels and facilities to have a Coast Guard issued identification credential or be escorted at all times.
According to Ed Merkle, director of port security and emergency operations, some people are one time visitors, such as truckers who have been trusted with bringing secure cargo across the country but do not have a TWIC card. The other challenge is when a TWIC card carrying person forgets his card for the day. These people would then need to be personally escorted to gain access to the port.
Trusted Agent will enable the authority to maintain TWIC compliance. The handheld device can notify dispatchers by communicating via Situator if the visitor with the device enters a restricted area, a section of the port he is not authorized to enter or if the device doesn't move for a pre-defined period of time. Such situational management tools are also “a good blend between physical and logical security,” added Merkle.
It also comes down to workflow, rules from the end-user so that the system has the ability to say what to do. And one byproduct of such an approach is the ability to hone routines and reprogram appropriate responses. Added Merkle, “On the fly, I wrote a set of instructions inside Situator for mass notification.”
Again, such tools provide both situational awareness and actionable information that matches the security mission with the business mission.
Major government systems integrators are catching the PSIM bug.
The City of Boston, for example, deployed enhanced situational awareness during April’s Boston Marathon.
Raytheon Integrated Defense Systems operationally deployed a system to integrate existing video, mapping, location, tracking and operational information into one common operating picture. Aimed at public safety and emergency management, Roderick Fraser, City of Boston fire commissioner, said, "This project demonstrated that we have the capacity to integrate current systems to provide better situational awareness in a geospatial way for all public safety agencies that we haven't had in the past."
SIDEBAR: Let Outsourcing Keep Up with Technology
When Ohio’s Medina County Federal Credit Union President Pete Grimm decided to take advantage of new security outsourcing solutions, he wasn’t necessarily looking to be the first. “I didn’t set out to be first,” Grimm said. “But the fact that we were had its benefits. We had the opportunity to really work with Diebold to customize solutions to meet our needs.” In today’s business environment, those needs were many. Grimm was working to balance the pressures of the financial market with the credit union’s vision to expand and grow its business. And while the organization viewed security as a priority, it didn’t have the luxury of a dedicated security staff. “Our goal is to have the best possible security at a price we can afford,” Grimm said. “It needs to be functional and easy to manage.”
Grimm didn’t have time to waste. Outsourcing is a creative approach to staffing that can enable organizations to overcome shrinking budgets and limited manpower. By adopting an outsourcing model, financial institutions can take advantage of a true, end-to-end solution while allowing for the addition of new security solutions with continually updated technology. And these benefits come without the traditional upfront expense.
Grimm didn’t have time to waste. Outsourcing is a creative approach to staffing that can enable organizations to overcome shrinking budgets and limited manpower. By adopting an outsourcing model, financial institutions can take advantage of a true, end-to-end solution while allowing for the addition of new security solutions with continually updated technology. And these benefits come without the traditional upfront expense.
SIDEBAR: Emergency Broadcasts also Crucial
There are some systems that are essential but may need to work apart but be connected to a total facility approach.
Intercom and public address systems have evolved into emergency communications systems at many facilities. They can range from tones that mean different things to pre-recorded and live speech. Depending on the facility or campus, there are discreet speakers and speakers built into emergency phone stanchions and the total system often boasts addressable units.
According to Rick Bull of East Stroudsburg University in Pennsylvania, the campus has a lot of emergency phones. “We have up to 90 emergency phones with some having sirens. All are from GAI-Tronics. There are pre-recordings and four different zones.” With about 7,000 students, the university’s security is administered by Chief of Police Robin Olson.
Added Bull, “Everyone has budget and resource challenges today. But we also have a growing population. Housing is a concern on and off campus. We are more and more urban – just an hour or so from New York City. Our police have a GAI-Tronics dispatch console that also handles the sirens and emergency public address needs.”
The emergency telephones and public address speakers must be intelligently placed to avoid both dead zones and bleeding into non-university territory.
Intercom and public address systems have evolved into emergency communications systems at many facilities. They can range from tones that mean different things to pre-recorded and live speech. Depending on the facility or campus, there are discreet speakers and speakers built into emergency phone stanchions and the total system often boasts addressable units.
According to Rick Bull of East Stroudsburg University in Pennsylvania, the campus has a lot of emergency phones. “We have up to 90 emergency phones with some having sirens. All are from GAI-Tronics. There are pre-recordings and four different zones.” With about 7,000 students, the university’s security is administered by Chief of Police Robin Olson.
Added Bull, “Everyone has budget and resource challenges today. But we also have a growing population. Housing is a concern on and off campus. We are more and more urban – just an hour or so from New York City. Our police have a GAI-Tronics dispatch console that also handles the sirens and emergency public address needs.”
The emergency telephones and public address speakers must be intelligently placed to avoid both dead zones and bleeding into non-university territory.
SIDEBAR: Video Advances Play Off of PSIM
Security video is at the heart – and the tricky part – of physical security information management. And imaging is moving ahead in many ways. Video analytic, whether at the edge or through centralized processing; megapixel cameras; 360 degree cameras (See article on Sentry 360 technology elsewhere it this issue.); and imaging coming from military developments.
For example, when the Department of Defense was looking for a way soldiers on armored vehicle patrol could see what a situation is before opening the door, one company came up with a 180 degree answer that has enterprise uses.
From Scallop Imaging, Digital Window is a seven megapixel surveillance camera that records in high resolution throughout its 180º field of view, without fisheye distortion. Employing five CMOS-based chips aimed in various directions, the system stitches together the images to transmit via MJPEG and H.264. The wall-mounted camera is extremely small and discrete.
For example, when the Department of Defense was looking for a way soldiers on armored vehicle patrol could see what a situation is before opening the door, one company came up with a 180 degree answer that has enterprise uses.
From Scallop Imaging, Digital Window is a seven megapixel surveillance camera that records in high resolution throughout its 180º field of view, without fisheye distortion. Employing five CMOS-based chips aimed in various directions, the system stitches together the images to transmit via MJPEG and H.264. The wall-mounted camera is extremely small and discrete.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







