Convergence 2.0
Today Convergence 2.0 is being driven by interdependency, efficiency and organizational simplification, security awareness, regulations, directives, standards and the evolving global communications infrastructure. Ironically, the current economic downturn will, according to security leaders, systems integrators and consultants interviewed for this article, speed up convergence.
“Convergence brings the opportunity for greater operational efficiency and the potential for contributions toward the organization’s profitability,” observed Robert Messemer, chief security officer at The Nielsen Company.
It also brings organizational changes.
TERMS MAKE A DIFFERENCE
Long-time consultant John Strauchs commented that “it is unfortunate that our industry appears to have been dubbed as ‘physical security’ (mostly by the IT folks I believe) so the term security isn’t confused with computer security, or IT security, or network security, or even electronic security. They even co-opted ‘intrusion detection.’ Physical security only describes one part of our technology -- the smallest part. I would rather our industry be termed building security or perhaps facility security, but I doubt that I will get many converts to my lexicon.”
Added Strauchs, “It’s important that some -- perhaps many -- manufacturers of security systems and equipment have not designed in comparable protection as have the manufacturers of computer and network hardware. Our security systems have been stand-alone systems for decades. Some IT managers are hostile to convergence because they see ‘physical security’ as a weak link. I have often heard it said that convergence in inevitable. I think that is an understatement. Convergence is here.”
That doesn’t mean that the definition of convergence has or will firm up soon.
For some, convergence is a fancy-pants term for security systems integration in which various security subsystems are connected beyond simple interfacing. For others, convergence means blending security systems with business systems such as point of sales for retail, employee training or traffic pattern analysis.
“From Dictionary.com: convergence,” said E. John Sutton, PSP, CPP, security & integration manager, security project management department, Port Authority of NY and NJ, “is the occurrence of two or more things coming together. Apply this simple but clear definition and all (typical) descriptions correctly represent convergence. Currently in our business it’s being used as a new buzzword to emphasize selected objectives. As always, care must be taken to ensure the components (the ‘things’ from our dictionary definition) are well defined to avoid misunderstanding/misinterpretation by our audience. Enterprise level systems combine many security functions within one system; this is convergence at some defined level. To consider impact to traditional security is somewhat of an oxymoron in that, for example, the combining of access control and CCTV assessment is a form of convergence yet has been in use for many years. It is a great term to use but to isolate and use of the word convergence without proper couching will inevitably lead to an undesirable result.”
COMING TOGETHER
In a general way, however, most security leaders see convergence as the bringing together of physical and logical – or computer – security in ways that primarily emphasize access controls and identity management.
Enterprise-impacted regulations also help push Convergence 2.0. The Sarbanes-Oxley Act, the Gramm-Leach-Bliley Act and the Health Insurance Portability and Accountability Act, for instance, require that certain data must be protected both physically and electronically and audited, too.
Still not everyone is on board yet.
According to “Enterprise Threat Management and Security Convergence: A Benchmarking Study,” significant barriers still exist that prevent organizations from converging their systems and many of these organizations remain conflicted on how to best attain optimal results. More than 50 chief information officers, chief security officers and chief information and security officers of U.S.-based global companies with revenues from $1 billion to more than $100 billion participated in the survey.
“The convergence of physical and traditional IT systems can provide compelling security benefits for an enterprise,” said Mark Diodati, identity and privacy strategies senior analyst with Burton Group, which conducted the survey for Honeywell. “Successful compliance initiatives can be enhanced when the organization adopts a holistic approach for managing access to these systems.”
INTERACTION HELPS
Most respondents indicated increased interaction between their security and IT functions:
- 63 percent said their security and IT organizations “had a formal coordination mechanism”
- 10 percent stated the two functions are run as one entity within their organizations
- 52 percent noted their security functions had a formal working relationship with their audit and compliance functions, while 11 percent said those functions are combined
The majority of respondents (nearly 73 percent) believe vulnerabilities in either physical or IT security can lead to a breach in the other system:
- 91 percent of the responding companies showed an increase in security investment
- 75 percent of which said those investments increased by more than 8 percent
- 31 percent suggested a greater than 12 percent rise
“This reinforces that companies are increasingly concerned with protecting their information assets as well as their physical assets, and they recognize that integrating once-disparate systems can be effective in addressing threats,” said Jim Ebzery, senior vice president of identity and security management at Novell. “How they choose to implement convergence varies on a number of factors including internal roles and overall attitudes about its effectiveness.”
Territory and infrastructure continue to play a role as Convergence 2.0 evolves.
When asked whether having physical security systems on IT backbones is a security risk, the answers in this study were split: 59 percent said "no" while 42 percent said "yes." The results also differed with regards to personal responsibility for organizing responses to a coordinated physical-IT security attack:
- 34 percent said there isn’t a single internal contact
- 27 percent said the director of security is responsible
- 14 percent said a single CSO deals with the threats
- 14 percent said the crisis management group is ultimately responsible
When asked to define “convergence,” survey responses varied from using IT backbones for security systems to automating manual processes through an IT system. Additional responses included the strategic partnership of physical and IT security organizations in risk management. According to Diodati, “The convergence of physical and logical systems has many moving parts. In addition, a convergence end state may look very different depending on an organization’s goals.
WILL IT REALLY HAPPEN?
Many more executives see convergence progress. Still there are those that believe the convergence of physical and logical security may never happen.
Thirty-three percent of respondents to the Burton Group study said they envision convergence happening within their organizations in the next two to five years, while another 33 percent said convergence will never happen. The barriers associated with true convergence include: turf control; complexity and skills needed to handle multiple disciplines; budget conflicts; compatibility across groups; lack of technical platforms and expanding privacy laws.
It all gets back to definitions.
It’s important to first distinguish between security convergence and the convergence of IT and physical security, said Steve Hunt, CPP CISSP, Security Magazine columnist and creator of the SecurityDreamer blog.
“It might sound like word play, but the highest level of convergence is merely the use of IT (computers, software and networking) to do physical security better. That creates a new breed of physical security products, like IP cameras, DVRs, NVRs, IP-based access control and managed services or hosted services,” Hunt said. The next tier of convergence, according to Hunt, is the convergence of physical security with IT.
Mo Hess, global segment manager, security, at TAC/Schneider Electric, agreed. “We see convergence coming from business and IT systems with security. More and more of security will be IP-based and on a network. Video, intrusion and access control have already converged in most large system applications.”
Writing in a recent Securitydreamer.com e-newsletter, Hunt acknowledges the impact of the economy on purchasing plans. This year will be a year of redoubled efforts to achieve efficiency and effectiveness. COOs, business unit managers and security executives will implement creative measures to complete necessary projects without creating new costs. “Clever managers know how to find money. By coordinating projects and working together with other business unit managers, funds may be pooled and tasks completed collectively. My clients have been especially successful at this sort of budget dollar ‘end run.’”
MERGING SUB-CULTURES
EMC Corporation’s Henry Hoyt, CISSP, noted that “Convergence as I have seen it variously used appears to be focused on the intransigence of merging two sub-cultures within a company or corporation and the needed transformation into one operational unit through the use of a common technology (tool kit). I think until organizational behavior (as used here -- a discipline) issues are addressed, the promise of what the technology could bring will be frustrated by two armed camps each defending their sacred ground.
“I think convergence somewhat misses any mark, however. What I witness resembles something closer to confrontation. Not the coalescing of interests that product marketing folks hoped to evoke. The physical security folks are being forced to perform more of their work where the assets and efforts of their client’s are located. Much of that asset base is now virtual or intangible. Add to that the displacement by digital technology of formerly analog protection and investigation tools places further pressure on the physical security folks to conform to or adopt means and methods that were once the domain of the information technology folks,” added Hoyt.
“I would point out that words like ‘security’ leave us with a very flat, one-dimensional view of a much richer and diverse work space. The trade-offs between alarm and protection are very different with, say, life safety versus information assurance.”
So the importance and future of security is converging with the business of business. Top executives have caught on. One high ranking banking security executive stated that when he thinks of convergence as it applies to information security, he thinks of “aligning information security to the business requirements, effectively converging and aligning information security with the business that it serves.”
Because of numerous reasons, presidents and chief executive officers of the most influential businesses better know their security operation, its return on investment and the real need to have professional security using appropriate technology.
A recent indicator: the Washington, D.C.-based Business Roundtable has an influential Security Task Force, which encourages private and public sectors to partner to improve security.
THE INTERNET PUSH
The Internet itself is helping to push Convergence 2.0.
Strengthening the Internet’s defenses against attack and recovering quickly following a major cyber incident will require IT venders, end-users and government to accept their shared responsibility and to work together, said Marian Hopkins, Business Roundtable policy director.
“Hardening the Internet is one of the most important security issues facing the business community,” Hopkins said. “So many of the critical systems impacting our security and our economy are being carried on a fragile cyber infrastructure, and we want to strengthen it.”
Companies have improved their cyber security, she said, but cannot stop making improvements to their systems because the threat continues to grow as well. Hopkins said that while end-users have a responsibility to keep their systems secure, CEOs also want better hardware and software that has fewer security flaws.
According to Salvatore D’Agostino of IDmachines and a member of the Smart Card Alliance, Federal Information Processing Standard 201 ( FIPS 201) is the basis for identity convergence. “This means adopting public key infrastructure and digital certificates as a common basis for strong authentication across domains. For those of us that work with the United States Government (at least in our case) it has become clear that we need to do for ourselves what we provide for others. And the faster we get out the FIPS 201 learning curve the more likely our organization and our clients will reap the benefits of convergence.
BUSINESS CONTINUITY
Emergency and disaster response is another Convergence 2.0 driver.
Business Roundtable has a Partnership for Disaster Response. Large U.S. companies have substantial financial, product and human resources that can be vitally important during a crisis and member CEOs are committed to using these resources to help communities prepare for, and rebuild from, disasters. The Partnership for Disaster Response was first activated immediately following Hurricane Katrina. As soon as Katrina struck, the Partnership began facilitating communications about critical on-the-ground needs and urged member companies to contribute to the relief effort.
Converged physical security, computer security and wired and wireless communications are at the heart of such responses.
Research firm Aberdeen Group has shown that through emerging capabilities in the area of security governance and risk management, best-in-class companies are taking proactive steps to ensure that their investments in security and compliance controls directly support their objectives for the business. A consistent, enterprise-wide view of security risk – integrating both physical security and IT security – is a sensible element of this strategy. By combining superior security governance and risk management with an integrated approach to logical and physical security, best-in-class organizations set themselves up to compete in the global economy with a distinct advantage: not only with an optimized IT infrastructure, but also with better protection for their digital, physical and human assets.
INTERACTIVITY AND CONVERGENCE
Interactive services will play a role in the evolution of convergence.
One recent example: ADT Security Services has a partnership with iControl Networks to develop new interactive services solutions which could revolutionize the way businesses are protected and managed. The agreement incorporates iControl’s next-generation platform into ADT’s monitoring network to provide life safety, lifestyle and productivity service enhancements planned for later this year.
The personalized solution integrates security, energy and lighting control, live video, event-driven video clips, pictures and a host of other functions. “Interactivity will help propel the way homes and businesses are secured and managed,” said Tricia Parks, chief executive officer of Parks Associates, a market research and consulting firm focused on emerging consumer technology and services. “This trend will drive incremental growth in the industry and provide security companies a platform to offer a variety of new services in the future.”
Risk management encourages cooperation and coordination: loss prevention, fraud prevention, business continuity planning, legal/regulatory compliance, insurance, to name a few. Bringing together those functions in some business way is part of convergence, too. The emerging title of chief security officer is a good start for some enterprises. It’s easier for the C-suite folks to talk with one person when they have a security question or concern, no matter if it is an incident in the parking garage or the data center.
IP video also is a more recent driver of Convergence 2.0.
Steve Taylor and Larry Hettick of Network World recently wrote that “the growth of video delivered over the Internet has grown dramatically over the last few years. For example, Cisco estimated that Internet video traffic in North America and Europe in October 2008 exceeded the amount of traffic that crossed the entire global Internet in October 2001.” Video over private enterprise networks is growing. According to Taylor and Hettick, Cisco recently disclosed in an analyst briefing that 60 percent of its internal network traffic is now video, and Cisco’s enterprise customers estimate that on average, the enterprise network demand for video capacity is growing at 50 percent annually.
FUTURE-PROOFING VIDEO CONVERGENCE INTO THE BUSINESS
Mike Thiel, director of security services for Children’s Hospital of Wisconsin, Milwaukee, had a vision of a flexible, future-proof converged video surveillance platform that could accommodate the hospital’s highly ambitious growth plans, incorporate existing infrastructure and hardware, deliver superior security and more. Thiel explained, “The security department is really undergoing an evolution of being an agent of change in supporting an organization growing at a breakneck speed. We want to be the trusted source of safety and emergency management within the health system, so our department needs to be out front of where the growth is going, we need to have a seat at the design table, and we need to be seen as more than just security.”
The hospital complex sees 8,000-10,000 visitors a day. The rapidly growing IP video surveillance system comprises over 250 cameras installed in five existing buildings and parking structures in the complex. An additional 80 cameras are being installed in the new construction of a 12-story tower scheduled to open in Spring 2009. All camera data as well as other security information is managed from the new Security Operations Center equipped with multiple workstations featuring 42-inch LCD screens. In addition to the cameras employed for security surveillance, Children’s Hospital is on the cutting edge of using the DVTel intelligent Security Operations Center (iSOC) to provide comprehensive security for their growing hospital complex and to support efforts to constantly improve and streamline patient care.
“We are creating a virtual Intensive Care Unit (ICU) capability,” said Thiel. “We are installing 72 pan-tilt-zoom cameras in our intensive care rooms that will enable physicians and other healthcare staff located elsewhere in the hospital complex to observe and zoom in to see what’s happening in each patient room. The cameras will have intercom capabilities so there will be two-way visual and audio interaction.”
Thiel continued, “We did not even know about the concept of ‘telemedicine’ when we choose the platform. Change is constant, so it’s impossible to predict the future. We could predict that we had to have a platform that is flexible, agile, and scalable.”
Cloud computing (see last month’s Security Magazine feature article), cluster storage from firms such as Intransa and Pivot3 and outsourcing all will push more security video across the enterprise and more convergence, too.
INTEGRATOR ROLE
Major systems integrators also see value in convergence.
Carey Boethel, senior director business development at Siemens Building Technologies, defines convergence more broadly. “Of course it is the technological convergence of independent technologies but it's also the organizational convergence of the security function. You can do all the technological investment but if you don’t have ownership or a champion higher up, you will never really deliver the value in convergence.”
Boethel agrees with others concerning the strength of convergence in today’s economic climate. “There has never been a time when efficiency is more important than today. It’s also the responsibility of systems integrators to bring an organization together.”
John Fenske, director of global product programs at Johnson Controls, urges security leaders to first consider business goals when viewing convergence. “There is a common framework in four areas: identity management, event management, building/energy management and compliance management.”
Fenske sees the turf war dust-up as an excuse. “Focusing on the business will bridge all those gaps naturally.”
The notion of converging physical and logical access security is not a new one. It has actually been around for some time, but historically, implementation has been a problem. Because physical and logical security systems have had little in common technologically, integrating them was a costly and complex proposition.
Richard Roop, CPP, director, programs at BAE Systems knows the challenges.
“Convergence of ‘physical and logical (computer) security,’ or ‘integrated security systems,’ or even ‘coming together of security and business systems’ is about gathering data, turning that data into information and applying information in a timely fashion for a given situation, what I refer to as knowledge management,” he said.
At BAE, enterprise convergence is routinely reviewed and updated to ensure “we are capturing the right data, at the right time for the right reasons. Additionally, we are looking at the process for converting that data into information for situational knowledge.”
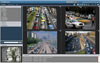
SIDEBAR: Call Convergence Collaboration
That’s what Adam Levine sees as the convergence of security systems and transportation management systems.
“The Joint Transportation Management Center (JTMC) in New York is a shining example of inter-agency communication, collaboration and responsiveness. By aligning personnel, procedures and policies on top of a comprehensive technology platform that leverages both new and existing infrastructure assets, we’re able to get the most timely and important information in the hands of decision makers when they need it.
“With a common operating picture, we’re better equipped to achieve our objective of safely and efficiently moving people, goods, services and information throughout the city and state of New York – and physical security information management (PSIM) software is the glue that brings the entire technology infrastructure together.”
In order to safely reduce congestion and efficiently move people, goods, services and information vital to the economy of both the State and City of New York, a strategy for a large, multi-stakeholder program for improved transportation safety and traffic management was developed including the build-out of a new Joint Transportation Management Center in Long Island City. This plan also specifically addressed the need to integrate existing field devices along with emerging technologies including wide ranging data sources and automated situation management to improve the performance of the overall traffic network.
So the New York City Department of Transportation undertook a multi-year program to implement an Advanced Transportation Management System for the majority of highways in New York City. As part of this program, a converged central video and control system was implemented at JTMC to monitor and manage all incidents within the New York Sub-region. The system provides one common operating picture for multi-agency coordination, including the New York City Department of Transportation and New York Police Department, which cost-effectively integrates and manages over 1,000 cameras and devices as well as all existing field equipment. VidShield, a multi-vendor video management application, provided by VidSys, facilitates centralized use and management of the deployed video assets and the selective presentation of live and recorded video streams. The Web-based application at the heart of the system collects, correlates, analyzes, formulates and distributes data as useful, intelligent information to the users through an operator client.
The software offers physical and logical connectivity, access and control of local and remote resources including traffic camera feeds, video walls, LCD monitors, audio-video systems, digital and analog matrix switches, video servers. Additionally, it interfaces with the Sub-Regional Management of Arterial Roadway Traffic System geographic mapping engine. This map interface allows any of the JTMC operators to access both legacy and new camera resources, via simple mouse clicks on the regional map.
SIDEBAR: What’s Web 2.0?
According to the Security Executive Council Web site (www.securityexecutivecouncil.com), Web 2.0 – as embodied in sites like del.icio.us, MySpace, YouTube, and Wikipedia -- may seem like a new technology that has exploded in the past few years. In reality it isn’t a technology revolution; it’s a revolution in the way existing technologies are used.
According to Tim O’Reilly, founder and CEO of O’Reilly Media, Inc., who is credited with coining the term Web 2.0 in 2004, Web 2.0 is a category of applications that meet the following seven criteria:
- They use the Web as a platform;
- They harness collective intelligence (they include content from users and other sites through tagging, permalinks, RSS, etc.);
- They are backed by specialized databases (such as Google’s Web crawl and Amazon’s product database);
- They are delivered as services, not products;
- They support lightweight programming models;
- They are not limited to use on a single device;
- They offer rich user experiences.
Web 2.0 is wikis, blogs, mashups, online document creation and collaboration, social networking, video and photo sharing. It is a philosophy of open online communication that is often interactive and user-driven. Many Web 2.0 programs are built using the scripting technique AJAX (Asynchronous JavaScript and XML), which works within the browser to speed page load time for the user.
Enterprises are adopting Web 2.0 applications in increasing numbers to improve communication and workflow within their businesses and to improve relationships with clients. The effort also creates security concerns that can be faced in a converged way.

SIDEBAR: Many Employees Undermine Traditional Data Breach Prevention Strategies
About 56 percent of U.S. business managers disable laptop encryption, increasing risk of data and identity theft. Welcome to the logical – or illogical – side of convergence.
Absolute Software and the Ponemon Institute told Security Magazine about the findings of a new study on the use of encryption on laptops by employees within corporations in the U.S. The study, “The Human Factor in Laptop Encryption: US Study,” revealed that more than half (56 percent) of business (non-IT) managers polled, disable the encryption solution on their laptops. Ninety-two percent of IT security practitioners report that someone in their organization has had a laptop lost or stolen and 71 percent report that it resulted in a data breach. Results indicate that it is employee behavior that undermines data protection efforts in corporate America.
“The data suggests that, because of user behavior, encryption alone is not enough to protect mobile devices and the sensitive data stored on them,” said Dr. Larry Ponemon, chairman and founder of The Ponemon Institute. “These statistics are especially disconcerting when combined with our recent studies demonstrating that lost or stolen laptops are the number one cause of data loss, with 3 out of 4 companies experiencing a data breach when a laptop has been lost or stolen.”
The report shows that many business managers fail to take necessary precautions to secure their laptops, such as using additional security solutions, and instead are overly dependent on their encryption solutions to protect the sensitive data on their laptops.
Key findings include:
- 92 percent of IT security practitioners report that someone in their organization has had a laptop lost or stolen and 71 percent report that it resulted in a data breach;
- 56 percent of business managers have disengaged their laptop’s encryption;
- Only 45 percent of IT security practitioners report that their organization was able to prove the contents of missing laptops were encrypted;
- Only 52 percent of business managers – employees most likely to have access to the most sensitive data (personally identifiable information and/or intellectual property) – have employer-provided encryption;
- 57 percent of business managers either keep a written record of their encryption password, or share it with others in case they forget it;
- 61 percent of business managers share their passwords, compared to only 4 percent of IT managers; and,
- Business managers are much more likely than IT security practitioners to believe encryption makes it unnecessary to use other security measures for laptop protection.
SIDEBAR: Enterprise Risk Management Reporting
John Petruzzi, CPP, CISM, vice president corporate security & emergency management at the giant Simon Property Group, sees organization value in convergence.
“In the early days, we defined convergence as bringing physical and logical security together, whether organizationally under one leader or via a committee chaired by a C-level executive. The reality is that for most small to large corporations as well as the government, convergence has already occurred: Physical security systems live and breathe on IT networks; investigators (traditional and IT forensic) collaborate to produce data of all shapes and sizes; numerous regulations require enhanced systematic reporting of both disciplines and so on.
“From a personal and professional perspective, convergence today is the continued dismantling of stove pipes, in other words, clear and constant collaboration amongst all departments which ultimately produces a clear and traceable path of organizational risks for CEO and other C-suite executives to consider. The end result is an organization which knows where its risky operations are and makes solid, well-informed business decisions based on its organizational appetite for risk.
“This is truly enterprise risk management, as security and safety professionals we need to remain focused on the creation of enterprise security risk management standards, policies and procedures which allow us to adequately report all operational risks to our C-suite counterparts. This includes but is not limited to physical risks, information risks and risk to the continuity of operations.”
Petruzzi drives home the business point.
“The security profession can only benefit from continued collaboration and integration with other business functions and the emerging requirement of enterprise reporting. Simply put, enterprise risk management will only increase the net value of our profession.”
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





