Protecting Enterprise Data on Mobile Systems with Trusted Computing
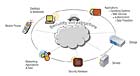
The big picture of TCG’s open-industry standards.
What is the Trusted Computing Group (TCG)? TCG is an industry organization formed to define, develop and promote open standards for trusted computing and security technologies, including hardware building blocks and software interfaces across multiple platforms, peripherals and handheld devices. TCG specifications enable secure computing environments without compromising functional integrity, privacy or individual rights. The primary goal is to help users protect their information assets (data, passwords, keys, etc.) from compromise due to external attack or physical theft.
TCG has developed three specifications to protect mobile devices and data from attack. Foremost is the Trusted Platform Module (TPM), a hardware building block for all computers from servers to laptops. The next is Trusted Network Connect (TNC), to protect enterprise networks from unauthorized users, and the most recent is the Mobile Trusted Module (MTM), developed by the TCG Mobile Phone Work Group to provide integrity, authentication and identity to mobile devices. MTM is the industry’s first open-standard specification for mobile devices.

Wireless Security Concerns Among IT Managers
Graph courtesy of Iain Gillott, iGR
Graph courtesy of Iain Gillott, iGR
SECURITY CHALLENGES
Authentication is an important element of trusted computing. Until recently, authentication meant deploying separate tokens or devices including smart cards, RSA Secure IDs, biometric readers or USB keys to each user. Because this approach meant incremental costs for purchase and support, they have been used only for specialized applications.Then the TPM appeared. It is a robust, standardized security chip that is integrated into the motherboard. It is now being sold in high volume in servers, PCs and laptops, and provides multifactor authentication as an integrated feature of the platform for virtually no additional cost. Some 50 million notebook and desktop PCs currently contain TPMs, enabling many security capabilities using existing hardware and applications.
The TPM stores keys, passwords and digital certificates and the stored information is secure against external software attack and theft. Security processes, such as digital signatures and key exchanges, are protected through secure TCG subsystems, i.e. access to data and secrets could be denied if the boot sequence is not as predicted.
Applications and functionality such as email, web access and data protection are secure with the TPM. PCs with TPMs allow users and their organizations to encrypt files (and entire drives), encrypt email and safely store certificates and passwords. Applications available for the TPM help users manage passwords and set up single sign-on, making systems more secure.
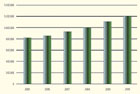
Worldwide Wireless and Mobile Handset
Shipments, 2005—2010.
Graph courtesy of Iain Gillott, iGR
Graph courtesy of Iain Gillott, iGR
TCGs CREATION–
Mobile Trusted Module
Mobile malware is becoming
a greater threat to smartphones, wireless PDAs and laptops. TCG’s Mobile Phone
Work Group developed a standard to enable mobile security that is embedded in
the device architecture and allows for interoperability with the existing
trusted computing framework. In 2006, TCG announced the industry’s first
open-standard specification, the Mobile Trusted Module (MTM), for mobile
devices.
The MTM consists of two separate modules: Mobile Local-Owner Trusted Module (MLTM) and Mobile Remote-Owner Trusted Module (MRTM).
The MTM modules protect data in local or remote mobile devices from online theft by leveraging TPM functionality and roots of trust, and by defining a subset of TPM commands for mobile use. Adding new MTM functions such as public key verification (PKI) provides further protection. The specification allows for ease of design and implementation in various mobile devices.

Brian Berger is an executive vice president for Wave Systems
Corp.
MOBILE DEVICE THREATS
Common threats to mobile devices are viruses, malware and Trojans, as well as identity or physical theft. User IDs and passwords are the weak link in any company’s security system. Identity theft does not include the hackers who steal thousands of personal records—rather the thieves who want a user’s name, ID and passwords. Corporate data theft is the leading threat to mobile devices.Mobile devices must have security functions that are cost-effective, transparent to users, reasonably implemented and interoperable. TCG’s Mobile Phone Work Group’s specifications fulfill these requirements by providing transparent and seamless security functions that are complementary to other security elements in place.
There are many benefits of TCG’s standards for mobile devices. Mobile devices will work as intended, while also preventing virtual and physical theft of data or unauthorized use of the device. Standards lower cost and stimulate the adoption of new systems, giving users more features and better security. Standards also enable easier and safer integration of work and leisure time.
The Trusted Computing Group will continue to develop and promote standards for computing building blocks and software interfaces across multiple platforms.
SIDEBAR: The Cost of Lost or Stolen Devices
The initial cost of lost or stolen mobile devices is the replacement of the lost or stolen device whether it is a mobile phone, PDA or laptop. In addition, someone (usually IT staff) determines if personal or corporate data has been compromised or stolen, plus restoring lost data to the device if it is still secure and usable by the owner.If the corporate network has suffered a security breach by an unauthorized user of a lost or stolen device, the device must be blacklisted, although any device can be altered to repurpose it to bypass network security.
Millions of people have had their personal information compromised because of lost or stolen systems, or because unauthorized users accessed data. Using available security technology would greatly reduce losses to organizations and their customers or employees.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







