Building Strong Policies for Ongoing Structure and Security
 In every element of our daily lives there are rules that guide our behavior. These rules come to us in many forms. From the time we are infants, our parents teach us what types of behaviors are acceptable and those that are not. We all remember the dreaded “No” from our mothers or fathers which was usually coupled with a stern look on their face. As we grew up, there were rules at school, and as we learned to drive there were traffic laws we needed to obey. Our world is full of legions of government regulations and laws with which we are expected to comply. We all understand that without rules, regulations and laws to guide behavior, civilization as we know it would cease to exist and we would be cast into a world of utter chaos.
In every element of our daily lives there are rules that guide our behavior. These rules come to us in many forms. From the time we are infants, our parents teach us what types of behaviors are acceptable and those that are not. We all remember the dreaded “No” from our mothers or fathers which was usually coupled with a stern look on their face. As we grew up, there were rules at school, and as we learned to drive there were traffic laws we needed to obey. Our world is full of legions of government regulations and laws with which we are expected to comply. We all understand that without rules, regulations and laws to guide behavior, civilization as we know it would cease to exist and we would be cast into a world of utter chaos.
Rules, regulations and laws give us that solid foundation to guide behavior and establish the consequences for failure to comply. As we entered the working world, things like codes of conduct, policies, procedures and processes were added to our list of things to guide us and to which we were expected to conform.
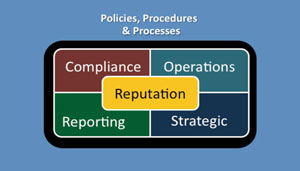
The outer ring of this graphic identifies key elements of establishing a solid foundation for implementing an Enterprise Risk Management (ERM) based program. This month we are focusing only on the area of establishing policies, procedures and processes.
Our working worlds are filled with complexity, whether you work for a company, an NGO, a non-profit or a governmental entity. Establishing rules of behavior and the consequences for failure to comply are critical to ensuring and maintaining any form of consistency and uniformity of actions across the enterprise. Policies, procedures and processes are necessary tools in defining the day-to-day rules of behavior and the steps that are necessary to get your job done efficiently, effectively and in a consistent manner.
Some organizations try desperately to create an open and free-wheeling environment in the belief that it will foster creativity and innovation. Somewhere along the way, unless it is a one-person entity, policies, procedures and processes will become necessary. Structure is a critical element to the working environment, just as it is to our everyday lives. Without structure, manufactured products would not be produced in a consistent manner, financial transactions would not be trusted and consistent failures would occur. These compliance failures not only can result in loss of trust in products or services, but can reach a level that breach laws and regulations. Ultimately, compliance failures can result in an erosion of the entity’s reputation and significant liability for not only the entity but also for those responsible.
There are a number of different ways to establish structure within an entity. We have all seen the proliferation of “Mission and Vision” at the top of the food chain in setting the overall operating philosophy for an entity. Some organizations have a very hierarchical structure, while others expect the individual elements of their organization to establish the ground rules for how to operate in those units. Establishing a set of high level policies that guide behavior and set the general standards across the organization is one of the best ways to lay the ground work for consistency across the entity. In the very hierarchical environment, top level policies are typically followed by procedure manuals for each of the various elements of the organization. This hierarchical approach many times leads to classic stove piping and does little for cross-fertilization of operating philosophies or expectations across the organization.
A more effective, but admittedly more complex, structure to track document change management is embedding compliance or operating requirements directly in each functional area’s operating procedures. For example: one approach is to require Procurement to reference the corporate security manual for guidance on the steps necessary to conduct a due diligence review of a potential supply chain partner. Perhaps a more proficient manner is to embed the steps necessary to conduct due diligence of potential supply chain partners directly in the procurement department manual.
One of the most effective ways to ensure people understand what is expected of them is by creating process flow charts and utilizing yes/no decision trees. The old saying “A picture is worth a thousand words” holds very true in today’s complex world.
This article was previously published in the print magazine as "Establish A Solid Foundation."
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






