Return of the Phone Phreakers: Business Communications Security in the Age of IP
|
|
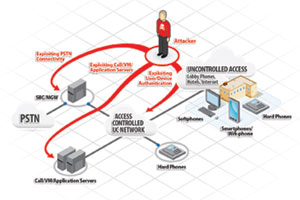
Figure 1: Three attack vectors in a typical company VoIP and SIP trunk environment resulting in toll fraud. |
Virtually every telecom manager in business today has received the pitch:
“Cut your telecom trunking costs by 50 percent. Improve your business communications flexibility. Take advantage of multiple competing telecom providers.”
The technological innovation underlying this promise is called SIP trunking, and it lives up to the promise when implemented properly and safely.
SIP trunking is a new way that a company can receive telecommunications services. Traditionally, a company achieved access to long distance services and other telecom services by hooking its telephone system up to “private lines,” ISDN lines, or other types of telecom lines called “trunks.” These provided access for the company’s communications into the public telephone network. Depending on how many calls the company wants to make and other factors, these trunking services could cost thousands of dollars per month.
But, over the past decade, business communications have been revolutionized by the arrival of broadband connections, giving companies high-speed access to the Internet. This innovation has also revolutionized voice services. Now, instead of a dedicated private line or ISDN link for trunking, a company can buy a virtual trunk called a “SIP Trunk” that rides over its broadband connection. SIP trunks can cost a fraction of the costs of traditional trunking, and many companies have made the move to SIP trunking for the cost savings.
At the same time, many companies have moved their business communications infrastructure to other Internet Protocol (IP) technologies, such as Voice-over-IP (VoIP). VoIP and SIP trunks are part of the same technological trend, as voice is moved to converged, IP-based data networks for both internal and external communications.
However, this new world of IP-based telecommunications has important security ramifications that must be understood and managed.
In fact, telecom security researchers over the past two years have reported a very sharp rise in attacks against unsecured VoIP systems. These attacks often take place over improperly secured SIP trunks that leave attack vectors open to be exploited by hackers, who, thanks to the Internet, can initiate attacks from virtually anywhere in the world.
Telecom attacks are certainly nothing new. As far back as the 1960s, hackers called “Phone Phreakers” were figuring out ways to fool the phone company’s telecom systems into granting them access to make long distance calls at no charge.

|
|
Adam Boone, VP of marketing for Sipera, says that consideration should be given to information security requirements in light of new IP-based communications. |
The Phone Phreakers are back. But in the age of IP communications, they can target systems in any country in the world, and exploit weak security in any company’s telecom systems if they are not properly protected. Consider these details about the trend in VoIP security breaches:
• Law enforcement authorities and fraud prevention groups in 2009 and 2010 described a sharp rise in toll fraud attacks, costing enterprises into the billions of dollars. Typical toll fraud attacks occur when a hacker finds an unprotected company phone system and takes control of it for a few hours. During that time, the attacker can actually sell access to the long distance or toll facilities to other, unsuspecting people, and run up hundreds of thousands of dollars in phone bills.
• The U.S. Federal Bureau of Investigation reported that a major international toll fraud ring operating in Europe and Asia had hacked more than 2,200 U.S.-based enterprises and committed fraud estimated to reach $55 million.
• Law enforcement authorities in Europe in late 2010 arrested dozens of hackers responsible for 11 million Euros in toll and premium rate fraud.
• IT trade journals and local media routinely report small companies receiving surprise long distance or charge call bills ranging from $10,000 to $100,000 or more. For a small business, such a bill can be crippling, and there typically is no way for the business to prove that these calls were not made by its employees.
• Industry researchers say that 1 in 4 hacking attacks utilizing the Internet are targeting VoIP systems and looking for improperly secured SIP trunks. Because the security safeguards at many companies have plugged the traditional hacking vectors, attackers have turned their attention to VoIP and SIP trunk vectors that are less well protected.
The three primary attack vectors related to toll fraud are illustrated in figure 1, which highlights that a toll fraud attack may take advantage of improper access controls, compromised phone systems, or even be the result of an internal user who has trusted status.
In addition to the toll fraud risks, there are many other security implications of the move to SIP trunks, VoIP and other IP-based communications.
VoIP is utilizing the same converged network that other applications are using, such as web-based applications and many others. This means that the voice traffic may be using the same corporate network as messaging, web browsing, email and many other applications. VoIP also can traverse the open Internet or other networks that are completely out of the company’s control.
From a security standpoint, this raises these issues:
• Unauthorized access: A typical practice is to separate the voice traffic from other traffic by a “virtual” network. But these virtual network protections are trivially easy to overcome using tools available for free on the Internet. Hackers have shown they can easily “hop” from the voice network on to the corporate data network and, by doing so, gain access to any database, system or computer attached to it.
• Eavesdropping: Because of performance concerns or the need to monitor and archive communications for compliance or quality purposes, the majority of enterprises choose not to use encryption for their VoIP traffic. Tools available for free on the Internet to any attacker make it easy for the attacker to capture and listen to an unencrypted VoIP call, and even forward that call to someone else.
• Compliance: A VoIP call may cross untrusted networks out of the enterprise’s control, or may be using end-user devices that are not controlled by the enterprise. Furthermore, VoIP calls are subject to the same regulatory rules are traditional phone calls. If your business is subject to privacy or archiving laws and deals with personal data of patients, students, legal clients, consumers, credit card users or many others, then encryption, monitoring and archiving of VoIP must be considered.
• Phishing, Vishing: VoIP calls that appear to come from a bank, for example, or another trusted institution will trick employees into revealing personal or corporate data to fraudsters and thieves, a crime called “Phishing” or “Vishing.” In 2010, U.S. law enforcement authorities issued warnings to consumers and business across many states that were being targeted by these attacks.
• Smartphones, tablets: The move to VoIP is also accompanied by the increasing proliferation of smartphones and other “smart” devices like tablet computers. Far from being simple phones like in previous generations, these devices are basically small computers, capable of running unauthorized programs, viruses and malware, and introducing these elements into the corporate communications environment.
Given all the security concerns noted here, a security director may wonder why a company would move to VoIP and IP communications at all. It would appear that the risks may outweigh the cost savings and benefits.
The good news is that the best practices for security in the VoIP and SIP trunk world have become well understood in the past couple of years. As with any new technology, the security risks and proper security safeguards can take time to emerge, as the new technology is adopted and put into widespread use.
For any information security manager, IT manager or security director whose company has moved into VoIP or SIP trunks, or is considering doing so, here are the best practices:
• Recognize that VoIP and SIP trunks are different from the technologies that they replace. Traditional voice networks are segregated from the bulk of corporate applications. Now that voice is moving to the converged, single IP-based network, IT personnel must plan carefully to ensure that voice communications remain confidential and controlled. The traditional data security architecture, such as data firewalls, is not designed for real-time applications like VoIP, and so cannot provide all the security safeguards required to secure the VoIP infrastructure.
• Evaluate information security requirements in light of the nature of these new applications. Now the same information that is utilized in a protected and encrypted application may be shared across the same network in a different, unprotected, unencrypted application. The result is that the security posture and policy has been undermined, and security directors must track these changes.
• Consider regulatory and compliance mandates. Even though a regulation may not specifically mention VoIP yet, regulatory bodies are providing firm guidance that VoIP and related applications should be considered and evaluated as part of the overall compliance process. For example, healthcare regulators who enforce HIPAA and the privacy requirements around patient data have directed that VoIP should always be encrypted as a security best practice. Similarly, the FDIC has advised banks and financial services firms that VoIP should be encrypted, among other safeguards.
A security director or IT security manager should insist that security is proactively planned as a company makes the move to VoIP, SIP trunks, or Unified Communications. This has benefits beyond the obvious improvement in security. A recent report by IT analyst firm Aberdeen Group found that companies that engage in VoIP security planning in advance of a deployment project will decrease overall project length by as much as a third. This is because a VoIP project that does not include proactive security planning will often end up being delayed or even derailed later when the security implications become glaring or introduce too much risk.
Four basic VoIP security requirements should be evaluated in the security architecture planning:
• Privacy: Encryption of all VoIP communications is a best practice and should be applied to all VoIP, both internal and external. But encryption is rarely deployed adequately because it can complicate architectures or introduce challenges to performance, compliance, and troubleshooting.
• Real-time policy enforcement: The application-layer firewalls or security components should be able to enforce security-related policies on traffic in real-time, so that security is maintained without affecting performance.
• Access control and user authentication: Robust authentication of users, their devices, and their access to systems and resources should be enforced in real-time. These controls need to reflect the fact that users may by accessing and using the VoIP applications using non-traditional devices and across untrusted networks, like the Internet.
• Threat detection and mitigation: Many companies have deployed Intrusion Detection and Intrusion Prevention Systems at the data level. These systems are often based on detecting the threat signatures for common data hacking attacks or malware, and they prevent these threats from reaching corporate systems. Thousands of such attacks have now been identified targeting VoIP and related applications, and a security best practice is to deploy intrusion mitigation to block these attacks as well.
A final best practice is for an enterprise to conduct periodic penetration testing that includes the VoIP and SIP trunking infrastructure and applications. Numerous security experts are available who specialize in this form of authorized VoIP penetration testing, which can uncover gaps in encryption or access controls that create an opening for eavesdropping, toll fraud or other attacks.
Each one of these areas is easily addressed with the latest generation of security products on the market or via consultation with the VoIP and Unified Communications security consultants now assisting companies with their VoIP security planning.
By proactively planning and managing the company’s VoIP security posture, an enterprise can safely and quickly adopt SIP trunks and VoIP, and not fall prey to the new generation of Phone Phreakers who are targeting these new technologies.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





