Neo-security: Inclusive Enterprise Risk Management
The emerging unified communications environment (including instant messaging, VoIP phones and TelePresence gear) create challenges for security and IT executives. Chart courtesy of Dimension Data
Yearning for the good old days? A nervous Jane stuffing her shopping bag with Preparation H. An over-confident Joe filling his pickup with goods off the loading dock. A vandal breaking into cars in the parking garage. Maybe even Sara the accountant cooking the books.
Forget about it.
Today chief security officers face risks not even imagined a few years ago.
The threat to enterprises from instant messaging. The extraordinary cost in time and dollars demanded by a discovery process involving company e-mails. The need to better protect documents from sophisticated thieves. And the expanded requirement to detect dirty bombs.
This tough new world offers myriad challenges.
“Ask any business leader to define security or risk management and you are very likely to receive a different response or nuance every time. That’s because, despite the wide use of expressions like security, risk management and enterprise risk management (ERM), there is no standard or accepted definition,” wrote former Deloitte CEO William Parrett in his just-released groundbreaking book, The Sentinel CEO. While he sees the chief security officer fast becoming a key decision maker in top management of many U.S. companies and an indispensable ally of the CEO, this new security and risk culture still must “transcend the silos and discreet function of organizations.”
That’s no easy task.
Avoiding the Silo
The silo approach to managing enterprise risk is inadequate because it leaves too many gaps and provides no reliable way to evaluate an enterprise’s risk position, according to a report by The Alliance for Enterprise Security Risk Management (AESRM), a partnership of leading international security associations – the Information Systems Audit and Control Association (ISACA) and ASIS International.The report, The Convergence of Physical and Information Security in the Context of Enterprise Risk Management, shows that while risk management is fundamental to most enterprise managers, many risk reduction initiatives are not coordinated or integrated across all risk areas. Only 19 percent of executives surveyed said their company has a robust process in place for identifying when risk tolerance approached or exceeded defined limits.
To address these risk challenges, organizations are investigating more inclusive ERM programs and converging traditional and information security functions. Although this convergence is intuitive and logical, it is still in its early stages, according to the research conducted by Deloitte.
“The need for enterprises to understand, measure and mitigate their risk is a leading factor driving the increase in security convergence,” said Ray O’Hara, CPP, chairman of AESRM. “Globalization and high-profile security breaches have gained the attention of boards and management, who increasingly realize how effective risk management protects their assets and supports growth.”
When asked to identify the major drivers of their companies’ security integration efforts, 73 percent of the executives cited “reducing risk of combined information and physical security threats,” 58 percent said “increased information sharing,” and 50 percent noted “better protection of the organization’s people, intellectual property and corporate assets.” The survey shows that security integration and ERM, when aligned, add value throughout an organization.
“Even though our study found that convergence is in its infancy, it is clearly a concept that is not going away,” said Adel Melek, global leader of the security and privacy practice at Deloitte Touche Tohmatsu. “But like any new idea, it takes pioneers or ‘visionaries’ to propel it forward.” Visionaries typically have a strong belief in the benefits of convergence and have the personal commitment to see their ideas to completion despite the uncharted territory in which they may find themselves.

Tech has come a long way, baby. A while back, a company introduced the Sensorama to get a person’s senses involved in a motion picture from wide vision and 3D to aromas and vibrations. Telepresence is the term that describes a new communications medium that enables a person to feel as if he or she is actually present in a different place or time. More recently, Cisco Systems’ TelePresence creates unique, in-person experiences between people, places and events in their work and personal lives. Cisco has built security into the system.
Solutions Emerge
Such visionaries aren’t working in a vacuum though. Solutions are emerging to energize them to contend with new threats.Don’t think you have a corporate chat problem? Think again.
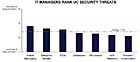
New research commissioned by Dimension Data reveals that unified communications is believed to be as secure as other technologies in the workplace. However, most end-users remain unaware of the potential risks they could be exposing their organizations to.
The research shows that 52 percent of IT users perceive unified communications to be as secure as most other information and communication technologies, while IT managers were more cautious, with 42 percent believing it was as secure.
And while end-users attribute similar levels of risk to all converged communications technologies, chief security officers and IT managers are more concerned with technologies that are harder to control – such as instant messaging (IM), enterprise mobility and PDAs.
Respondents “rated IM as having the highest risk, probably because of the high levels of uncontrolled public IM already prevalent in corporate environments,” said Gavin Hill at Dimension Data. “The research indicates that 67 percent of end-users surveyed use IM at home and work, but only 35 percent of companies formally offer this as a corporate tool today.
“While enterprise-grade tools are available, many organizations still allow employees to use public tools in the environment. Placing unified communications technologies in the hands of end-users who are unaware of the risks and corporate policies could result in the benefits being offset by the increased risk and security threats in the corporate environment,” he told Security Magazine.

Unified Communications Have Challenges
In the next two years, unified communications will be a reality in most organizations, and with high levels of adoption being driven by the “consumerization” of IT, companies cannot afford to ignore the need for risk prevention strategies and education. “Interestingly, end-users perceive e-mail as the biggest security risk and give little consideration to other risks such as theft of service, identity theft and eavesdropping,” Hill said.Hill also pointed out that user education and change management around the best use of unified communication technologies was critical. “This will ensure that employees are aware of the potential security risks and leverage productivity opportunities that can be gained from using these technologies,” he said. Dimension Data’s unified communications study was conducted by Datamonitor.
IM may be the tornado on the horizon but it’s corporate e-mail that, for many organizations, is the storm that’s arrived. Threats are e-mailed inside and from outside enterprises. Viruses can come as attachments. Spam clogs up mailboxes and servers.
Still, the e-mail security task gets really tough when so-called discovery requests and accompanying requirements hit the CEO’s desk. Not only are there legal risks but the security and IT operations often are hit hard.

By eliminating the need to restore from backups, PSTs and e-mail servers, an e-mail archive is becoming a requirement for businesses that want to safely respond to discovery requests for legal and business reasons.
Tracking E-mail
According to a survey by Osterman Research for e-mail archiving provider Fortiva, for example, such discovery requests are putting a significant strain on enterprise resources. The survey shows that security and IT departments face an average of 20 litigation-related requests annually; for organizations with over 1,000 employees that number jumps to 32 litigation-related requests each year. In addition to legal discovery requests, there are an average of 36 business requests, 24 regulatory or audit-related requests and 108 end-user requests annually.Retrieving raw e-mail data for a single legal discovery request takes almost a month and this doesn’t take into account the time required for a legal review of the data. “Sometimes the CEO may decide to settle litigation or a regulatory case because his or her organization cannot find the e-mail records or cannot find them in time,” Eric Goodwin, CEO of Fortiva, told Security Magazine.
“Based on our research, 75 percent of businesses are still relying on backup tapes to recover information for discovery. This is concerning not only because tapes can be very time-consuming to restore, but also because they have a high rate of failure and corruption – which can make it impossible to satisfy a request,” added Michael Osterman of Osterman Research. “By eliminating the need to restore from backups, PSTs (Personal Storage Table files; Microsoft Outlook saves e-mail information in .pst file on a computer or server.) or e-mail servers, an e-mail archive is becoming a requirement for businesses that want to safely respond to discovery requests for legal and business reasons.”
Other findings from the survey include:
- In addition to being time-consuming, discovery requests are having a negative impact on other projects. One in four businesses surveyed has delayed a business or IT initiative in order to meet legal discovery requirements.
- For each discovery request, over half of the time spent by security and IT (58 percent) is spent gathering, restoring and searching through backups, while the remainder is spent finding and searching through PST files (25 percent) and searching through the e-mail server (17 percent).
- On average, businesses keep 24 months’ worth of data on backup tapes.
- Security and IT departments bear the bulk of the costs of recovering data for legal discovery, representing an average of 62 percent of the total costs involved.
Of course, many organizations have security headaches over paper-based documents in addition to the electronic versions.

Paper documents need better security, too. There are numerous cost-effective security methodologies that not only are extremely difficult to replicate or reverse engineer, but also allow for easy verification of authenticity.
Better Protecting Documents
The best-known example is the $100 bill, the most counterfeited document in the world. The U.S. Department of the Treasury recently said it was redoing the bill’s design to add even more diverse types of security features. That strategy is shared by many corporations wishing to protect their own documents.For example, the 3rd annual Print Excellence and Knowledge (PEAK) Award’s big winner was a bilingual oil drilling inspection certificate designed with security features to protect against fraud. According to the award's judges, the finished piece showed a custom document with a range of security features from low to high. “This has a lot of features that make it harder to get through,” the judges said. “When it comes to document security, you have to overkill and this has it.” The award went to ProDocumentSolutions.
The document was produced on a true watermark paper with unique security images embedded into the paper. The images can only be viewed by translucent “pass through light.” There are other in-paper security features, including chemical protection from special color indicators that react to chemicals, blue and red visible fibers and invisible fluorescent fibers. The paper also has a special toner adhesion coating that more securely anchors images to the paper, thereby making it more difficult to remove images without visible damage to the paper.
Corporate security also can choose from other document protections.
- Anti-copy backgrounds that use a microscopic text and numerical algorithm to easily authenticate a transcript. Most warning backgrounds use dots or lines, which are easy to copy.
- Printed in heat-sensitive ink, instant interactive verification means that touching, briskly rubbing or breathing on the area verifies color changes and the hidden word “VALID.”
- Optical variable pixel holograms with the word “SAFE” ghosted into it. When viewed at different angles, four distinctly different images are visible. It’s fused into the substrate, so removal is impossible without destroying the paper.

The newest employee is the chief security officer, an indispensable ally of the CEO, according to William Parrett.
SIDEBAR: Integrating Security and Risk
Change is underway. “Risk management is evolving to become integrated into a company’s strategic activities and corporate culture, more lateral thinking to imagine the unimaginable is emerging, and companies are dealing more and more with anti-western sentiments,” said William Parrett, Deloitte’s former CEO and now senior partner. “To help preserve value, companies need to go beyond managing risks in silos and create an integrated organization-wide risk management function. Although risk can never be eliminated, companies that implement a more comprehensive approach to their control environment will be better placed to prevent, minimize or recover from losses in shareholder value,” added Parrett in his book The Sentinel CEO: Perspectives on Security, Risk and Leadership in a Post-9/11 World.SIDEBAR: It’s Your Extortionist Calling
During this past summer, there have been more than 25 incidents of attempted extortion by telephone, in which businesses report receiving a telephone call threatening to set off a bomb while demanding the store wire money overseas. In several cases, the businesses complied. And in numerous incidents, the callers suggested they had broken into local store security cameras to monitor their long-distant hostages. Law enforcement officials report that these original events have spurred copycats. Investigators believe the calls are coming from western and eastern Europe.
A dirty bomb can be inside a suitcase left on the street. New detection systems are emerging for use by corporations and institutions as well as law enforcement.
SIDEBAR: “Dirty Bomb” in a Suitcase
Experts in the U.S. Department of Homeland Security have plenty of worries. One of the biggest is the threat from a so-called dirty bomb.A dirty bomb is one type of a “radiological dispersal device” or RDD that combines a conventional explosive, such as dynamite, with radioactive material. Most RDDs would not release enough radiation to kill people or cause severe illness - the conventional explosive itself would be more harmful to individuals than the radioactive material. However, depending on the scenario, an RDD explosion could create fear and panic, contaminate property, and require potentially costly cleanup.
A dirty bomb is not a “Weapon of Mass Destruction” but a “Weapon of Mass Disruption,” where contamination and anxiety are the terrorists’ major objectives.
Underlining the corporate concerns about dirty bombs, there were new-age detection systems displayed at last month’s ASIS International event in Las Vegas.
For example, V-RADS from Vidiation is gamma radiation detection technology that identifies radioactive materials by analyzing streams of surveillance video.
It is estimated 60-90 curies of radiological material is all that is needed to build a dirty bomb. There are thousands of sites that store or use radiological materials in medical, industrial or manufacturing settings that can be used for the construction of a dirty bomb, with many of these locations relatively unprotected. V-RADS uses information generated when high-energy gamma rays and particles interact with the image sensors of security cameras; its proprietary algorithms and expert system analyze data and identify radiation that may pose a security threat.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





