The Endpoint is the Point

Think for a minute about all the computers, laptops, servers, phones and PDAs humming and chirping around your campus. Employees and contractors are walking around, sitting in conference rooms and cubicles, and milling around data centers with these gizmos.
And nearly every one of them is connected to the company network in one way or another. Add those little memory sticks to the mix – you know, the thumb drives you shove into the USB ports on the computer to copy or backup files – and you have a world of security trouble on your hands.
Every one of those devices can knock a company right out of regulatory compliance, or slap the CEO onto the front page of the Wall Street Journal with some explosive loss of all your customers’ identity information. It’s time you took notice and did something about securing these "endpoints" to prevent information leakage.
Technology Options
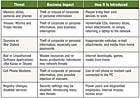
Your network folks may already have deployed some security tools. Let’s look at what they might have out there.Vulnerability Scanners detect network problems but cannot adequately assess how endpoints may be improperly used.
What they do.Vulnerability scanners provide network-based scans of thousands of vulnerability sources. Nessus, the most popular freely downloadable network scanner can find thousands of known vulnerabilities and are most useful in large networks.
What they don’t do.
Vulnerability scanners do not provide active protection of devices, nor are they designed to respond to brand new exploits and alone cannot assess many vulnerabilities on PCs or other endpoints.
Auditing Tools collect local logs of events and compare events to policies.
What they do.An audit tool will create a report of violations of policy on networks or PCs. They periodically scan the network for unusual traffic patterns or problems and probe for any weaknesses. NetIQ or Symantec Compliance Manager can check for weak passwords or improper rights given to system administrators and discover security related activities on PCs.
What they don’t do.
Audit tools do actively correct problems they discover or control behavior on a PC. They do not work without client software running on each device. Ugh.
Network Admission Control Systems offer limited inspections of basic security settings on PCs and devices connecting to the network.
What they do.Known as NAC from Cisco or NAP from Microsoft (standing for Network Access Protection), these systems perform inspections of PCs as they connect to the network checking for current versions of antivirus and anti-spyware software and other security settings.
What they don’t do.
NAC inspections do not detect many threats related to information leakage.
Client Firewalls control network connections on a PC.
What they do.Also known as personal firewalls, these software products monitor connections to and from the PC by Internet sites, software applications, and external devices. I use Check Point Software’s Zone Alarm but Symantec’s Sygate Enterprise Protection is also good. Consider going on the Internet to get colleague reviews of these products and others mentioned.
What they don’t do.
Client firewalls cannot prevent a user from disabling the firewall or changing security settings. They usually just protect against a few of the most common Internet threats.
Device Protection focuses on appropriate use of attached devices but largely ignore how applications are used.
What they do.Products from SecureWave, Controlguard, Safend and others monitor and control use of memory sticks and some software applications and external connections.
What they don’t do.
Device protection software doesn’t prevent attacks from a device authorized by the system or by a connection not actively inhibited by the software.
Disk Encryption protects against losing information when a laptop or PDA is lost or stolen.
What they do.Hundreds of people can attest to the feeling of satisfaction they had when, after recovering from the shock of losing a laptop, remembering that the hard drive was encrypted. Utimaco and PointSec do a good job of enterprise-wide hard drive encryption, but both lack a way of securing a document once it leaves the PC.
What they don’t do.
Disk encryption does not protect information once it leaves the computer as an email or when it is copied to a memory stick.
Nature of the Solution
The technology options to address all these threats can make your head spin. But in fact, there is a simple and affordable way to manage the problem. Promisec makes a software product that choreographs all of those security solutions listed above. Its Spectator Pro product watches all installed security products, like client firewalls, antivirus and information leakage products, fixing a variety of problems that naturally arise. Frequent scans of devices from the network reveal when security products are not doing their jobs. Maybe the client firewall is disabled, or perhaps the anti-spyware is not installed, or antivirus is out of date. Maybe a user of the machine attached a storage device and downloaded personal information of customers. Spectator Pro alerts security personnel and may automatically send signals to network access control systems, or antivirus servers, and so forth, to initiate either a quarantine of the non-compliant system or full repair and update of the machine.When information leaves the safe confines of the company loaded onto a physical device, it’s your problem. Now you have an easy way to keep your boss (and yourself) out of trouble and your company’s information safe.

SIDEBAR
Build Redundancy Into Disaster Plans, Too
Whether you are protecting your computers and data from attack or staff from natural or man-made disasters, redundancy is the key, according to Susan Sparkes-Hoskins at Gunnar Manufacturing, Calgary, Canada.Protection begins outside at the interface with the world around:
1. Landscaping designed to slow and allow for video monitoring and identification of those approaching the building including structures erected keeping cars from encroaching on the building.
2. Structural facades of buildings provide reinforced protection against terrorist attacks and provide greater strength against natural disasters.
3. Windows in buildings are either bullet resistant or treated with a protective coating to help contain glass fragmentation.
4. Security officers, electronic access control systems and even metal detectors positioned at all entrances.
AND THEN WHAT?
If the lines of defense to this point are breached, where do your employees turn to for safety? We have always been told, that in case of disaster to hide under a table or other strong structure in the hope of finding a void and having your life spared.Now, we can take most of the luck out of the equation and ensure that you have your own purposeful void under your desk.
5. A safe and secure place to seek refuge in the event of a building collapse due to natural disaster or terrorist strike.
There are now on the market protective office furniture systems which reduce risk and enhance the probability of survival in the event of a building collapse due to natural disaster, criminal activity or terror attacks through several features contained in a unique, patented design. Such office suites are covered in a composite material that acts as a protective coating to hold the desk together so it does not become additional shrapnel and pose a danger to everyone around it.
Some even have a personal protection pod with a Kevlar coating. Such desks bolt to the concrete flooring so they don’t become projectiles.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!




.webp?height=200&t=1769044794&width=200)

