When Pop Culture Drives Mobile App Development, What Happens to the Security of User Data?
Today, mobile apps are as ubiquitous as beer, music and fashion. In fact, they are so popular that they now define how we as a culture communicate new trends and participate in fast-moving memes. However, like a viral infection, mobile applications, if kept unsanitary, have the potential to spread protected user data across the internet with the same public exposure as the celebrities those users idolize.
First let’s set the stage:
Mobile Apps = Pop Culture (and more)
Pop Culture = Volume (fans, apps, speed of adoption) and Income
Volume and Income = Incentive for Attacks
Let’s review these concepts above in action:
Mobile Apps = Pop Culture (and more)
According to VentureBeat, mobile applications are already a $40B industry and can grow to $70B by 2017 (see image) without a single industry profoundly affected by this growth.
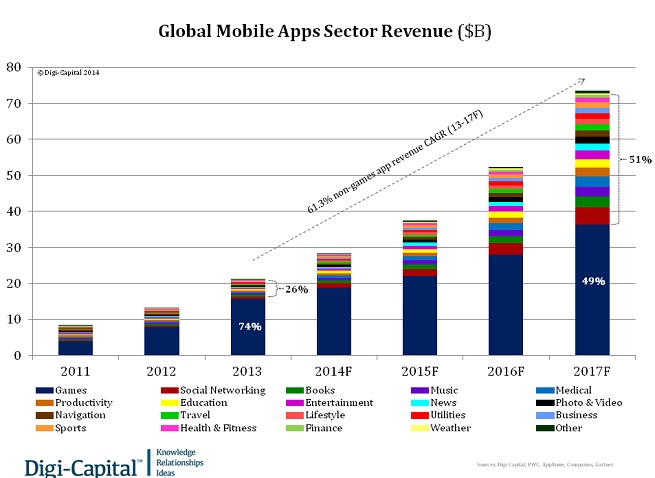
Consumers use mobile apps to support every part of their lives, from ordering pizza to tracking their exercise routines, to managing their money. The consumption and sharing of popular culture is no exception. Likewise, when celebrities race to release mobile apps that engage and communicate with their fan base, people adopt these apps and incorporate them into their daily lives. Pop culture sensations, the Kardashians, recently released mobile apps to engage with their fans with unmitigated success.
If you are not familiar with this particular Mobile App’s business model, they're effectively Web TV channels for each sister, featuring videos, diaries and a variety of lifestyle content.
In fact, Apptopia, a firm specializing in Mobile App usage, estimates that more than 1.5 million people downloaded Kylie Jenner’s app in the first five days. That's well ahead of 398,000 downloads for Khloe Kardashian, 362,000 for Kim Kardashian, and 216,000 for Kendall Jenner. Moreover, an analysis shared with CNNMoney by Apptopia shows that Kylie's app could make $15 million in its first year as each app costs $3 a month.
Pop Culture = Volume (fans, apps, speed of adoption) and Income
So how popular are Mobile apps in putting things into perspective? Well, not quite as popular as beer – yet! (See graphic below or here.) However, according to forecasted projections, Mobile Apps will close in on surpassing the beer industry sometime by 2019-2020.

But what are the dangers?
The Kardashian/Jenner Mobile Apps were brought to market in record speed – so quickly that they launched with a misconfiguration leading to some highlighted flaws in Apple’s Mobile App store. These flaws are not really easy to uncover because they are not exploits from known vulnerabilities (which are far more easily enumerated and cataloged). However, this design flaw exposes protected user data to anyone that can discover it – basically creating a huge vulnerability in the app’s security and a huge liability for the Kardashian/Jenner family.
By exposing the flaw in the design of these apps, we have identified a challenge well beyond the popularity of the Kardashians. Often the decision to bring an app to market is determined based on the desire to capture market share, disrupt an existing market, or – in the case of celebrity – to capitalize on an emerging trend. These priorities will drive a development team to rush to market – unfortunately, with rush there is inherent risk.
No matter how secure a company typically is, they need to take a step back and remember that protecting their users should be the top corporate responsibility on their list. Clearly there is an obvious tug-of-war between speed-to-market and security in the application space. However, a quickly selling Mobile App is a Pyrrhic victory if in the pursuit of speed to market a rushed vulnerability destroys the very delivery infrastructure built to support it.
Volume and Income = Incentive for Attacks
Clearly we understand that Apps, which conduct commerce, will always be rife for attacks. We also understand that Mobile Apps which house important information (like user emails, phone numbers, credit card data, Social Security numbers, etc.) that can be commoditized are also highly risky for cyberattacks. However, is it well understood that high volume or highly popular Mobile Apps are equally or maybe more desirable then the first two Mobile App Characteristics as they allow an attacker to achieve scale and scope.
Widely deployed apps can easily be used, in conjunction with automated software programs, DDoS tools, Advanced Persistent Threat vectors and malicious code infiltration resources. Simply said, Mobile Apps like the Kardashians’ and Jenners’ make perfect platforms for nefarious actors to conduct their seedy operations in a more obfuscated manner.
So, given that, here’s a quick punch list of things which should make you feel comfortable about a Mobile App’s security:
- The Mobile App’s End User License Agreement (EULA) documentation provides you with certain rights as an end-user for data privacy and restitution of grievances caused you by the site.
- The Mobile App’s activation process explains how the data will be used and stored and why it is being requested. In addition, the process should detail what elements of phone will be used in providing the Mobile App service – such as location and contact list information.
-
Strong authentication. If the Mobile App doesn’t support strong authentication then it is a weak application. What is strong authentication – it’s combining any two (or more) of the following data as part of your authentication into the application:
- Something you know (e.g. Password)
- Somewhere you are (e.g. geo-location against a predetermined knowledge of where you SHOULD be)
- Something you have (e.g. a physical key or device which aids in authentication when used in combination with other data)
- Something you are (e.g. biometric data)
- Does the Mobile Application address platform security risks, including keychain on iPhone (option to store passwords) and access to payment applications?
- Review the Data at Rest processes and procedures. For example, do they enable permanent deletion of user data? Is the data stored in an encrypted format always? What type of encryption?
- Review the Data in Transit. Is the Mobile Application using current encryption algorithms such as TLS 1.2 and avoiding transmitting sensitive user data over insecure WiFi networks?
- Does the Mobile Application authenticate non-human interactions such as APIs and legimate bots?
- Does the application provide you with options to access current security tools to conduct routine assessments of the Mobile Application’s current security status?
- Does the Application maintain any industry-level security certifications such as PCI or routine scans visible to the public?
In the end, we must acknowledge that Mobile App hacks are an eventuality and information security is a life-long session of cat and mouse games. Human desire to usurp is matched by an equally powerful motivation to secure. So which one wins? The one we pay more attention to.