Enterprise-Wide Alignment Drives Contract or Proprietary Decision

The
mission of security officers has expanded and embedded more deeply in the
enterprise. Photo courtesy of Wackenhut Corporation
While the debate continues between contracted and proprietary officer operations at the nation’s largest enterprises, those of both sides of the argument stress the need for quality personnel, continuing training and a constantly expanding business-centric role for security officers beyond typical patrols.

Contract
security has its place. But is that place with you organization?, questioned
Brad Hellums, CPP, CPO, security manager, Trammell Crow Company, and one of
Security Magazine’s 25 Most Influential executives in 2006.
He is vice president of security and loss prevention for General Growth Properties, the second largest U.S.-based publicly traded Real Estate Investment Trust (REIT). General Growth currently has an ownership interest in or management responsibility for a portfolio of more than 200 shopping malls in 44 states, as well as ownership in planned community developments and commercial office buildings. The portfolio totals approximately 200 million square feet of retail space and includes more than 24,000 retail stores nationwide.

Nicholas
Luciano of Hannon Security Services advises that “Not all contract security
firms are created equal.”
BALANCING THE PLAN
With such an intense and sprawling mission, Levenberg depends on contracted firms for parking lot, parking garage and public area security. In malls, typically tenant stores provide their own level of security in their areas.David Levenberg’s experience with contract officer firms is mirrored in the details of a national stuffy conducted just a few months ago.
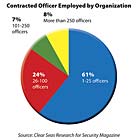
According to the results, nearly six in ten security executives (56 percent) who are Security Magazine readers contract their guarding needs while another 24 percent have a mix of proprietary and contracted officers. While most of those surveyed by Clear Seas Research for Security Magazine (61 percent) have 25 or less contracted security officers, eight percent of survey respondents who contact officers have 250 or more officers assigned.
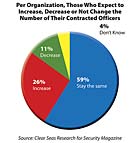
There is evidence that contract guarding services will grow in the future. While nearly six in ten (59 percent) who contract out the service say the number of officers will stay the same in the future, a healthy 26 percent report they intend to increase officer ranks.

Electronic
security has added a new dimension to the tasks and training of security
officers.
Going beyond the typical patrols, contract security officers cover building lobbies (61 percent), monitor a central station (37 percent), investigate incidents (31 percent) and provide courier services (18 percent). Based on results of the Clear Seas Research for Security Magazine, there also is growth in the use of contracted officers as executive bodyguards.
Quality of the service and pricing are the top reasons that would trigger a change in the contracted guard firm. Two-thirds of respondents who have contracted officers say that a negative event would be the trigger, while 38 percent say that a price increase who make them consider another guard firm.

EMPLOYEE ADVANTAGES
On the other hand, many security executives see value in hiring their own officers.“Security providers are abundant, and there is a price to fit every need. But what seems to suffer most with a drop in price is the commensurate drop in quality. To be sure, contract security has its place. But is that place with your organization?” questioned Brad Hellums, CPP, CPO, security manager, Trammell Crow Company, and one of Security Magazine’s 25 Most Influential executives in 2006.
Hellums suggested that CSOs consider six elements:
- How well trained are the people you are looking to put in your organization?
- How vested are they in the success of your organization?
- What guarantee is in place that good people will be retained?
- What incentives can a low paid employee find to continue at your organization if the financial rewards or benefits are non-existent with the contractor?
- What image does your organization wish to project to its customers or clients?
- Is it important to see the same people regularly, or is constant rotation of people at your location acceptable to you and your customers or clients?
John Rankin, CPP, of G4S Security Services (Canada) Ltd., realizes that deciding between using an outside contractor to provide security and going “in- house” has challenged many managers over the years.
CONTRACT ADVANTAGES
Rankin has his own points that point to contract security.Training: who will be the trainer? Will they be competent to train in many security functions; where will the courses come from? Will they meet government standards?
Human Resources: Who will hire, background check, license, maintain records, scheduling, deal with unionization, discipline or terminations?
Liability: who will take responsibility in a legal action? Has everything been done in order to not be found negligent and have all aspects been addressed in relation to personal safety? Have we met minimum standards on training; do post orders cover all aspects related to the specific job specifications?
Backup: who will cover for vacation, illness, last minute book off, no shows, resignations, and emergencies?
Supervision: How will you ensure all shifts are supervised; who can attend the site after hours in case of an emergency?

Nicholas Luciano of Hannon Security Services also sees value in contract security officers but with a twist. “Not all contract security firms are created equal. It is the responsibility of the buyer to properly research and hire a quality security firm with a solid background. The phrase ‘you get what you pay for’ is especially true when it comes to hiring people who manage other people. Hire a partner, not just a vendor.”
“Contract security companies recruit, screen, hire, train and supervise security personnel. From the time we wake until the time we go to bed, and sometimes in the middle of the night, everything we do is all geared to enhancing the tasks we perform. If security is not your company’s core competency, this job will be better performed and supported by people who focus on it relentlessly,” he pointed out.

Complementing Security Magazine’s guard survey, Luciano also sees that a contract company will be able to provide additional resources that will enhance an enterprise security department or program, (i.e. investigations, security audits, executive protection, patrol services or alarm response services). He added, “A good contract security provider can share best practice policies and procedures and connect you with other similar companies to promote networking.”
About the Survey
All research findings/results included in the above article are from the Clear Seas Research 2007 Contract Guard Study. For more information about these and additional findings found in the comprehensive study, including report pricing, please refer to www.clearseasresearch.com, write: info@clearseasresearch.com or contact Renee Love at (248) 786-1581.Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






