Using NIST for Easier Cybersecurity Management
Corporate executives can develop enough expertise to comfortably navigate key cybersecurity risk management concepts




In last month’s column, we proposed that cybersecurity is a business necessity that requires C-Suite attention. Security readers likely agree that thinking of cybersecurity merely as an IT issue “is similar to believing that a company’s entire workforce, from the CEO down, is just one big HR issue.” This month, we will explore how corporate executives, including the owners of small and medium businesses, can develop enough expertise to comfortably navigate key cybersecurity risk management concepts. Most important, there is no need to speak geek or to spend any money.
You’ve Heard of the NIST Framework. Now, Use It!
When the National Institute of Standards and Technology (NIST) does something, it tends to go all out. So, when the President of the United States asked (okay, he directed) NIST to develop a cybersecurity framework, the group left no stone unturned. In fact, over the course of a year, NIST worked with more than 3,000 individuals and organizations on standards, best practices and guidelines before publishing their final document. The result is freely available at www.nist.gov/cyberframework. Not including the Appendix, it is only 17 pages long. Surely you can find the time to read 17 pages!
Strengthen Your Core
NIST developed parts of the framework as a roadmap for officer and director engagement. Specifically, the framework identifies five high-level functions to “provide a concise way for senior executives and others to distill the fundamental concepts of cybersecurity risk so that they can assess how identified risks are managed, and how their organization stacks up at a high level against existing cybersecurity standards, guidelines and practices.”
After gaining an understanding of the five functions, executives might open up the conversation by asking their team these questions:
- How do we identify our critical data and services, and the risks associated with them? (Look for answers involving asset management, governance and risk assessments.)
- How do we protect our critical data and services from harm? (Listen for a range of technical, physical and administrative controls.)
- What technologies and personnel do we have in place to detect the occurrence of a cybersecurity event that bypasses our protections? (Consider what aspects of your network activities are continuously monitored, and whether logging activities actually are reviewed.)?
- How will we respond to a detected cybersecurity event? (At a minimum, answers should refer to and be gleaned from an Incident Response Plan.)
- How would we recover from a cyber incident in a timely manner? (Determine the extent of your business continuity and resilience planning and training.)
Tiers for Attention
NIST also proposes that businesses consider a four-tier system to help determine whether their cyber risk management processes, their enterprise-wide integration and their external partnerships are (1) only partial, ad hoc, reactive, stove-piped and insular; (2) risk-informed, prioritized, enterprise-aware and partner-aware; (3) repeatable, formalized, updated and collaborative across the enterprise and with external partners; or, (4) adaptive, continuously aware and continuously improved through lessons learned.
Although the tier system has the look and feel of a classic maturity model, NIST rejects that term since progression to higher tiers only is encouraged “when such a change would reduce cybersecurity risk and be cost effective.” Phrased differently, just because something can be done to lower security risk, does not mean that the NIST framework requires that it be done. This approach is quite different, for example, than a standard that would require all technically possible cybersecurity measures be implemented. Instead, the NIST approach implicitly acknowledges that even a good risk management process can result in a bad cybersecurity event. The unfortunate truth being that some risks never will be eliminated. Still, although NIST steers clear of requiring specific controls for specific situations, the framework offers little or no refuge to officers, directors or business owners who fail to engage actively and continuously in a detailed evaluative process.
Get With The Program
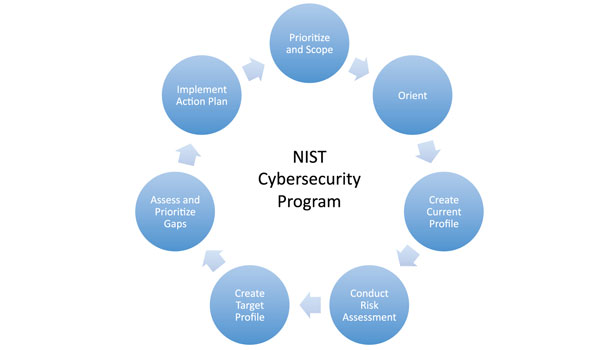
Putting it all together, NIST identifies a seven-step cycle for creating a cybersecurity program. The first step is for the executive team to identify organizational mission priorities, to determine the scope of systems and assets that support the selected business line or process and to make strategic decisions regarding how best to control them. Second, organizations must identify the business dependencies of their systems and assets (and those of third parties), together with legal requirements, threat actor intelligence and identified vulnerabilities. Third, organizations should create a current profile regarding each of the five high-level “core” functions discussed earlier. Fourth, organizations should conduct a risk assessment that incorporates “emerging risks and threat and vulnerability data to facilitate a robust understanding of the likelihood and impact of cybersecurity events.” Fifth, the organization is to develop a target profile of desired cybersecurity outcomes, followed by the sixth stage of determining, analyzing and prioritizing the gaps between the company’s current and target profiles. The seventh step is for the organization to develop and implement an action plan to reduce the gaps. Then, repeat.
Conclusion
If cybersecurity is not already the focus of your C-Suite, it soon will be. Although the benefits of the NIST framework are not limited to the cyber uninitiated, it certainly offers them an excellent place to start.
About the Columnist: Steven Chabinsky is General Counsel and Chief Risk Officer for CrowdStrike, a big-data cybersecurity technology firm that specializes in continuous threat monitoring, intelligence reporting, cyber security assessments and incident response. He previously served as Deputy Assistant Director of the FBI’s Cyber Division.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!