Edge Smarts Demands Incident Analysis
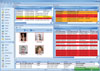
An incident reporting and risk management system allows a casino to bring together access control and security video incident reports into one display. Casinos have two separate systems – security and surveillance – that must remain separate. But incident reporting can bring together data for a total review for action and improvement.
With security access decision making, like security video, at the edge, there is a shift to incident reporting and analysis and its cousin, physical security information management (PSIM).
Incident reporting has long been a security procedure but has been recently souped up with computer-based tools. It’s a way to categorize what has happened and reach conclusions for better protection.
For example, Prairie Band Casino and Resort considered the various options for an incident reporting and risk management system and chose iView System’s iTrak Incident Reporting Platform.
The system has given the business the ability to go paperless. No more making unnecessary copies. All you have to do is simply log in and view the details of the daily activities. Having a multiple client access system enables all regulatory departments to sign on and review both security and surveillance reports, eliminating the need for paper reports and reducing the cost of purchasing paper to print out the reports.
Incident reporting has long been a security procedure but has been recently souped up with computer-based tools. It’s a way to categorize what has happened and reach conclusions for better protection.
For example, Prairie Band Casino and Resort considered the various options for an incident reporting and risk management system and chose iView System’s iTrak Incident Reporting Platform.
The system has given the business the ability to go paperless. No more making unnecessary copies. All you have to do is simply log in and view the details of the daily activities. Having a multiple client access system enables all regulatory departments to sign on and review both security and surveillance reports, eliminating the need for paper reports and reducing the cost of purchasing paper to print out the reports.
SHARING THE REPORTING SYSTEM
Incident reporting allowed both security and surveillance to share a common system. The security department’s main issue was they were using an outdated Microsoft Access database that only allowed them to create reports with no capability to integrate other programs, thus creating more paperwork and record storage issues.
Michael Jackson, director of security, said, “The software allows us to bring together all of our reports in one system. Another major reason was the ability to add additional modules in the future like risk management that automatically connects to the system without worry.”
Together with dispatch and a lost & found module, Prairie Band Casino and Resort has an all in one solution that allows both security and surveillance to share a fully converged platform. This enables both departments to create their own reports, with the capability to share information, while ensuring all regulatory procedures are followed.
PSIM is a “while it is happening” tool to help provide the best response.
There is a heavy buzz over PSIM.
But as Gavin Long of BAE Systems pointed out, “When the buzz takes place, numerous people begin to latch on to language. The language of PSIM is now being more fluently used and, unfortunately I think, can create some confusion. It’s really the placing into one system the intelligence to give people who are managing the situations all they need to understand the situation quickly. It’s providing analyzed, intelligent information that’s actually necessary for a response and, one step further, to create better policies to what we’ve learned through that system of information sharing, information integration.”
Michael Jackson, director of security, said, “The software allows us to bring together all of our reports in one system. Another major reason was the ability to add additional modules in the future like risk management that automatically connects to the system without worry.”
Together with dispatch and a lost & found module, Prairie Band Casino and Resort has an all in one solution that allows both security and surveillance to share a fully converged platform. This enables both departments to create their own reports, with the capability to share information, while ensuring all regulatory procedures are followed.
PSIM is a “while it is happening” tool to help provide the best response.
There is a heavy buzz over PSIM.
But as Gavin Long of BAE Systems pointed out, “When the buzz takes place, numerous people begin to latch on to language. The language of PSIM is now being more fluently used and, unfortunately I think, can create some confusion. It’s really the placing into one system the intelligence to give people who are managing the situations all they need to understand the situation quickly. It’s providing analyzed, intelligent information that’s actually necessary for a response and, one step further, to create better policies to what we’ve learned through that system of information sharing, information integration.”
TOTAL INTEGRATION
PSIM must integrate applications and devices from multiple vendors. It must leverage the enterprise infrastructure investments. PSIM also must be preventative and reactive, not just limited to forensics, according to Long, who added that it must gather, analyze, disseminate mobile data, “including, I would say especially video. Video in this environment is the most difficult area to manage.” PSIM must reduce data flow and technological concerns to empower the security leader.
David Fowler of VidSys has a number of essentials of physical security information systems.
“The first is the ability to collect all of the information from the physical security devices. We typically find when we get into an organization that they not only have a lot of different devices that they want to communicate with, whether NVRs or access control systems or RFID or sensor environments or building control, but they also have this equipment from multiple vendors and the difficulty they struggle with is how to collect the information from all these different systems and bring it all together.”
He added that it is also important to integrate in a way to actually analyze the information as it’s coming in.
David Fowler of VidSys has a number of essentials of physical security information systems.
“The first is the ability to collect all of the information from the physical security devices. We typically find when we get into an organization that they not only have a lot of different devices that they want to communicate with, whether NVRs or access control systems or RFID or sensor environments or building control, but they also have this equipment from multiple vendors and the difficulty they struggle with is how to collect the information from all these different systems and bring it all together.”
He added that it is also important to integrate in a way to actually analyze the information as it’s coming in.
FROM BOOK TO AUTOMATION
The goal in any PSIM system is to take what would normally be the standard operating procedure in a book and get it into the system. Not just in the form of a static document, but actually in a form of activities that can be executed either automatically by the system or manually by an operator.
Karen Steinfeld at Raytheon agreed. “PSIM is really not about a bunch of disparate applications that are stitched together, but it’s about a single integrated solution that allows security leaders to effectively manage and resolve situations. So planning for that by having a system that’s based on open standards is very important. Open standards will allow you to more easily integrate the pieces as technology needs arise. The other piece is scalability. Even without the need for new applications and services, there is going to always be an increased demand for bandwidth and for numbers of users on a system.” Her point: Leverage existing investments where possible. “And that means really doing an assessment of what assets you have and what the remaining useful life is and how they would fit into your solution that you have planned going forward.”
A pilot program in the quad-cities area of Illinois and Iowa that Raytheon was involved proves the benefits of an integrated PSIM solution that would really improve both the communication and the information sharing ability of the public safety agencies within this area. The quad cities are really two different states, encompasses Iowa and Illinois, four major cities and a population greater than 400,000 people. So it’s a good sized area that faces a lot of the same challenges that most cities in mid-America face. “What the quad cities looked to do was first to go and form a governance model that brought these jurisdictions together so that they could work together and share information and honestly what we learned was that was the hardest part,” said Steinfeld.
The second challenge was developing network solutions to enhance the region’s infrastructure in terms of voice and video and data communications. “So we brought in a number of things in addition to the video surveillance. We had license plate recognition, we had interoperable communications gateways, collaboration tools, and a number of other applications including patient tracking that were available on the wireless network. So a fully integrated solution provided the situational awareness and gave the public safety officials the ability to respond more effectively.”
Karen Steinfeld at Raytheon agreed. “PSIM is really not about a bunch of disparate applications that are stitched together, but it’s about a single integrated solution that allows security leaders to effectively manage and resolve situations. So planning for that by having a system that’s based on open standards is very important. Open standards will allow you to more easily integrate the pieces as technology needs arise. The other piece is scalability. Even without the need for new applications and services, there is going to always be an increased demand for bandwidth and for numbers of users on a system.” Her point: Leverage existing investments where possible. “And that means really doing an assessment of what assets you have and what the remaining useful life is and how they would fit into your solution that you have planned going forward.”
A pilot program in the quad-cities area of Illinois and Iowa that Raytheon was involved proves the benefits of an integrated PSIM solution that would really improve both the communication and the information sharing ability of the public safety agencies within this area. The quad cities are really two different states, encompasses Iowa and Illinois, four major cities and a population greater than 400,000 people. So it’s a good sized area that faces a lot of the same challenges that most cities in mid-America face. “What the quad cities looked to do was first to go and form a governance model that brought these jurisdictions together so that they could work together and share information and honestly what we learned was that was the hardest part,” said Steinfeld.
The second challenge was developing network solutions to enhance the region’s infrastructure in terms of voice and video and data communications. “So we brought in a number of things in addition to the video surveillance. We had license plate recognition, we had interoperable communications gateways, collaboration tools, and a number of other applications including patient tracking that were available on the wireless network. So a fully integrated solution provided the situational awareness and gave the public safety officials the ability to respond more effectively.”
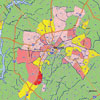
A new crime vulnerability database from CAP Index compared 2008 and 2009 information and found that, among changes, crime has shifted noticeably from inner cities to sprawling suburban areas. Pictured is Charlotte 2008 at top and 2009.
SIDEBAR: The Ultimate: Crime Forecasting
A number of crime forecasting tools, fed with crime statistics and other data, can help security leaders determine vulnerability of their facility locations or a potential acquisition location or proposed new site.
One such service, CAP Index, just introduced its 2009 Crimecast crime vulnerability database. At the advent of the recent economic downturn, the firm anticipated a dramatic shift in crime. The new model reflects rapidly changing patterns of crime across the country and reveals some surprising shifts about where that crime is occurring.
For example, there has been an up tick on robberies, property crime, shoplifting and larcenies in business. It addition, there has been a movement from the inner cities to sprawling suburban areas as housing moved out.
The updated database is the culmination of a two-year long development process. “When signs of weakness in the housing market first began appearing, we anticipated that early softness in this arena would have a long and deep impact on the overall economy, and that this sustained downturn could cause some dramatic – even unanticipated – shifts in crime,” said Jon D. Groussman.
One such service, CAP Index, just introduced its 2009 Crimecast crime vulnerability database. At the advent of the recent economic downturn, the firm anticipated a dramatic shift in crime. The new model reflects rapidly changing patterns of crime across the country and reveals some surprising shifts about where that crime is occurring.
For example, there has been an up tick on robberies, property crime, shoplifting and larcenies in business. It addition, there has been a movement from the inner cities to sprawling suburban areas as housing moved out.
The updated database is the culmination of a two-year long development process. “When signs of weakness in the housing market first began appearing, we anticipated that early softness in this arena would have a long and deep impact on the overall economy, and that this sustained downturn could cause some dramatic – even unanticipated – shifts in crime,” said Jon D. Groussman.
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!







