Silicon Valley Bank (SVB), a major U.S. bank that provided financial services to some of the largest and most well-known tech investors and startups, collapsed on Friday, March 10. It was taken over by federal regulators under the control of the Federal Deposit Insurance Corporation (FDIC) after depositors rushed to withdraw billions of dollars in deposits from the bank.
A financial crisis of this magnitude quickly gains worldwide attention and interest from hackers who see chaos and stress as a point of opportunity. As bad actors prey on customer fear amid the bank's collapse, security leaders have begun to see a series of phishing campaigns impersonating SVB.
Financial online services are a prime target for phishing attacks
Phishing attacks are attempts by cybercriminals to trick individuals into divulging sensitive information such as login credentials or financial data from emails, text messages, or websites that appear legitimate but are fake. In the context of online financial services, phishing attacks may use fake login pages or emails to impersonate the real financial institution to trick victims into providing sensitive information that can be used for criminal activities such as identity theft or financial fraud. In some cases, the victims are redirected to the real site, so they mistakenly think they are interacting with the financial institute but are unwittingly giving their credentials to attackers.
SVB phishing campaign analysis
With attackers creating domains that closely resemble the name of the targeted organization, it is no surprise that SVB is at the center of an emerging phishing campaign. These domains may contain minor variations and often include references to financial terms, such as payments or financial aid, to trick individuals into clicking on malicious links.
As in many phishing campaigns, hackers have been testing their malicious domains before deploying them to ensure they work effectively. As it appears, one of the attackers is from Turkey, as they were able to lure a local target to their website just a few hours after purchasing the domain.
More than 90 new SVG domains have been register to be used in attacks against targets, mainly in the U.S.
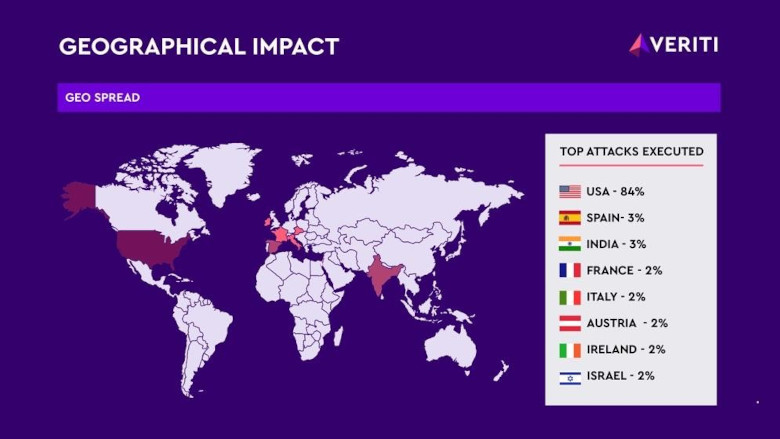 Image via Veriti
Image via Veriti
Credit Suisse and First Republic Bank are now in the crosshairs
The collapse of SVB triggered a crisis of confidence that has led to several banks around the world facing significant stock hits. Credit Suisse and First Republic Bank are the latest, with Credit Suisse borrowing up to $54 billion from Switzerland’s central bank and First Republic Bank receiving a $30 billion capital infusion from fellow lenders to bolster confidence in the financial system.
As the situation continues to unfold, SVB-related phishing campaigns are starting to decrease in volume, while new phishing campaigns related to Credit Suisse and First Republic Bank are already in the works.
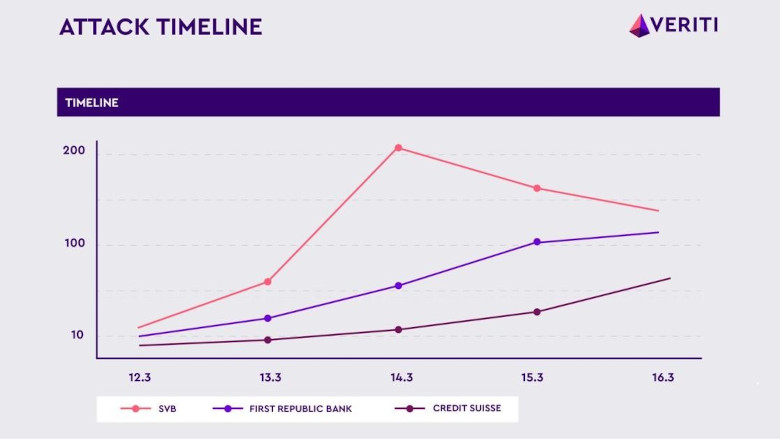 Image via Veriti
Image via VeritiHackers again are taking advantage of the uncertainty around the stability of Credit Suisse and First Republic Bank, which makes their customers more susceptible to phishing attacks.
How to avoid being the next victim
Hackers prey on the fact that security leaders throw the security rulebook out the window in a moment of stress or that they are not paying close attention. Don’t let them win. Security leaders need to think rationally and follow the best practices and encourage employees to do the same, especially with attacks like this that are difficult to detect.
Be vigilant – Take extra precautions by reviewing URLs on any web pages that ask for log-in details or financial information. There are nearly 100 new SVB-related domains, and the numbers are growing as we speak. Be wary of unsolicited emails, misspellings and clunky web pages.
Maximize existing security tools – There might already be an anti-phishing tool within an employee’s security stack and they don’t even realize it. Scan the resources that are already built into the environment and ensure everything is turned on, properly configured with alerts, and updated with the latest malicious phishing URLs, including email security, network, and endpoint security, browser protection and URL/domain filtering.
Re-visit cybersecurity awareness training – Training should always be part of a security leader’s first line of defense. Cybersecurity threats will continue evolving in their complexity and prevalence, so don’t wait until it’s too late. Make sure employees are undergoing training on a regular basis.
Not only is having a robust security stack that’s designed to detect behavioral anomalies critical but so is making sure that a environment is fully optimized. Invest the time and energy now because tomorrow will surely bring the latest shiny and new phishing hook.




