One out of every two on-premises databases globally has at least one vulnerability, finds a new study from Imperva Research Labs spanning 27,000 on-prem databases.
Joseph Carson, chief security scientist and Advisory CISO at ThycoticCentrify, explains, “It comes as no surprise that many organizations still struggle to patch systems and reduce critical vulnerabilities, especially on databases. The balance between productivity and security is always a fine line. When databases are offline, it typically means the business productivity is impacted. Databases can contain sensitive information such as employee data, personal identifiable information, health data, financial details, intellectual property and much more, so organizations must protect and secure databases with the highest priority. While the report does include some concerning numbers, it does not tell the complete picture as while the number of vulnerabilities is high, and it does not detail other security controls used to protect those databases. Patching systems is critical, but it is also important to have strong access controls using privileged access security along with detailed auditing and MFA.”
The research uncovered several notable trends:
Organizations aren’t maintaining regular patching: With nearly half of all databases globally (46%) containing a vulnerability and the average number of Common Vulnerabilities and Exposures (CVEs) per database standing at 26, it’s clear that businesses are ignoring one of the basic tenets of data security which is to patch and update databases as soon and often as possible. We’ve even identified vulnerabilities that have gone unpatched for more than three years — an incredible amount of time considering the sensitivity and value of data. The volume of CVEs present in most databases means that hackers now have dozens of well-known, easily exploitable paths to businesses’ most sensitive data. Indeed, today hackers have to search tools like ExploitDB to find proof of concept code that allows them to exploit such vulnerabilities.
Severe vulnerabilities are being ignored: More than half of the vulnerabilities present in databases globally are ranked as either ‘High’ or ‘Critical’ severity according to NIST guidelines — vulnerabilities that allow attackers to, amongst other things, steal or manipulate sensitive data, take control or move laterally through the network once the database is compromised. Not only are businesses not investing enough effort into patching, but it seems some databases have just gone unnoticed as we identified CVEs dating back three and four years.
Geography matters: While the global figures are concerning, the regional breakdown is even more worrisome for industrialized countries like France, Singapore and China. The databases in these nations all have vulnerabilities that exceed the global average, both in terms of the percentage of databases that are vulnerable and the average number of vulnerabilities per database. However, the average number of vulnerabilities is still relatively high even for countries like Germany, which have a relatively low percentage of vulnerable databases (19%). Thus, improvements are still needed.
Hank Schless, Senior Manager, Security Solutions at Lookout, says, “Even as the cloud has taken over the way we store and access data, there will always be a certain amount of on-prem infrastructure and applications that need to be monitored and secured. For many industries and organizations, this is because of compliance reasons. Or simply because it would be too much of an undertaking to move a massive amount of critical infrastructure and data to the cloud.
“There are several risks involved in keeping things on-prem, especially from the security perspective. This report points out one of the most glaring challenges of on-prem: implementing security patches for vulnerable databases and other infrastructure. Organizations need to rely on their admins to download and install these patches as they’re made available. While admins may be diligent in doing so, it’s almost inevitable that they’ll miss a couple of resources. In that case, one vulnerable database is just as bad as one hundred. In addition, on-prem services may reach an age where they’re no longer supported. With few exceptions, this means that they will not receive a patch if additional vulnerabilities are discovered after they’re no longer supported.”
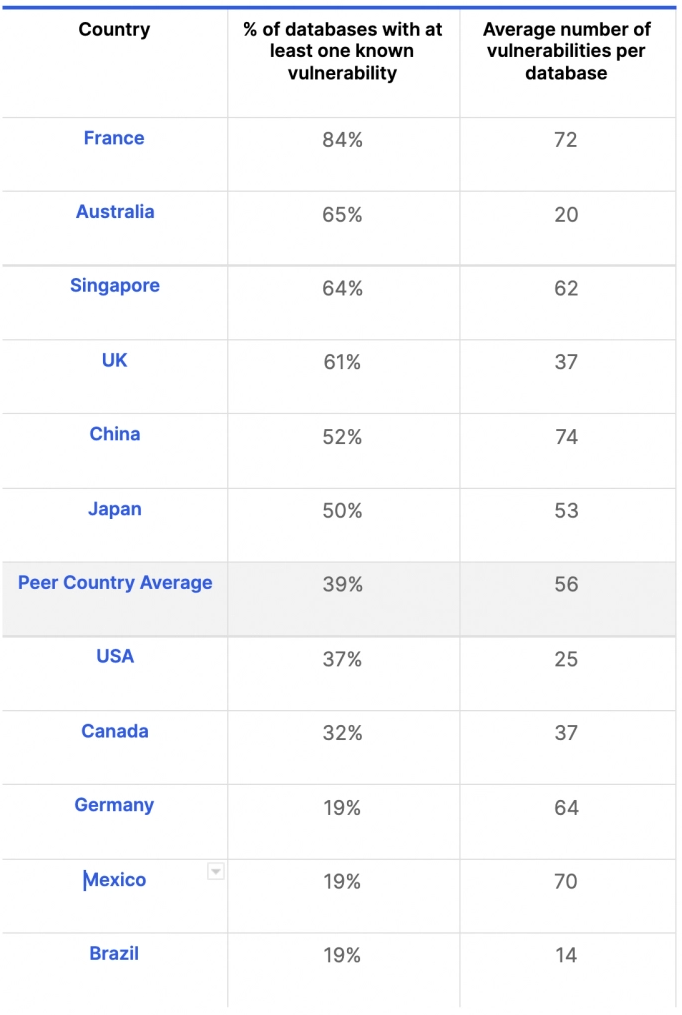
Image courtesy of Imperva
“In some respects, for those of us who’ve managed the chaos that exists inside an enterprise, these numbers aren’t surprising,” says Tim Wade, Technical Director, CTO Team at Vectra. “Certainly, the presence of neglect and a lack of IT hygiene are an important part of this finding, but it’s equally important to contextualize these findings against the reality that databases are disproportionately a part of essential business systems relative to other infrastructure. This reality creates tension between the risks of disruption via exploitation from failing to patch and the inevitable cases where patches aren’t fully baked and can cause disruption. This tension exposes how the notion that enterprises will simply dig their way out of security holes with vulnerability management is a work of speculative fiction – known and unknown vulnerabilities will always exist in some noteworthy quantity, exploitation will occur as a byproduct of this, and it is incumbent on security professionals to invest in the capabilities necessary to detect and respond to such inevitabilities before material damage is done.”
Yaniv Bar-Dayan, CEO and co-founder at Vulcan Cyber, says security teams have three options to address data security:
- Do nothing and play the odds. This option isn’t acceptable to most organizations, but as we can see from Imperva’s research is the path almost half of all on-prem database administrators have chosen.
- Outsource to a data service like AWS or Snowflake. This doesn’t completely absolve the data owners from security responsibilities, but it goes a long way to reduce the burden. Cloud and data lake services can still be hacked through user configuration errors or faulty user access control vulnerabilities. But the DBaaS service providers operate their cyber risk management and vulnerability remediation programs at the highest levels of program maturity, which provides much-needed relief for many organizations who don’t want to own these responsibilities.
- Be like the data service providers and attain a “transformative” level of risk mitigation and vulnerability remediation maturity. There are four risk and vulnerability remediation program maturity levels, with “reactive” being the least mature and “transformative” being the most mature at level 4. Vulcan Cyber research finds that 55% of vulnerability management programs are at maturity level 1 or level 2, which draws a direct parallel to the prevalence of known, but unresolved, on-premises database vulnerabilities.
Keep in mind, Bar-Dayan notes, “that even though a database might contain a vulnerability, it doesn’t necessarily mean that the vulnerability poses a significant risk to the business. There is a chance the database security team is doing their job right and has identified the vulnerability, assessed the threat against the database assets, and prioritized it at a non-critical level of risk to the business.”
The Imperva data, explains Bar-Dayan, doesn’t show if the vulnerabilities are acceptable based on the owner’s assessment of risk, and vulnerability severity according to NIST guidelines is simply one input into a meaningful custom risk score to the end user. Risk-based vulnerability prioritization is essential for effective data security.
Schless adds, “Even if an organization’s infrastructure, apps and data have to remain on-prem to some extent, the IT and security teams can still take a modern approach to secure them. Typically, access to these resources has been done through VPN, but nowadays, even VPN solutions are being found to have vulnerabilities in them. The modern approach to securing access to on-prem and private apps or infrastructure is leveraging zero-trust network access (ZTNA). In doing so, organizations can extend the security benefits of the cloud to on-prem services. Most importantly, it enables teams to build dynamic access policies that take into account contextual signals such as the user, location, device OS and profile, user and device risk score, and more to determine whether the on-prem resources are safe to access. Users can access on-prem resources from any location and device, whether managed or unmanaged, without needing to hairpin traffic. ZTNA also enables teams to cloak their internet-facing private apps to prevent them from being discovered by attackers crawling the internet for vulnerable assets.
“Implementing ZTNA enables teams to include on-prem resources in their zero trust architecture and move towards a modern approach to securing the interactions between users, devices, networks and data,” says Schless.



