Home » Publications » Security Magazine
Security Magazine

2013 December
Cover Story
Back to TopTechnology has become ingrained in enterprise security operations.
Read More
Featured Articles
Back to TopHow Emergency Messaging Aids Access Strategies
Getting the word out, correctly, in time and to the right people, is an important mission for colleges and universities.
December 1, 2013
How Mesh Networks Form the Backbone of Smart Cities
Wireless mesh networking is not for everyone. But, when it makes business sense, it works the best.
December 1, 2013
The Future of Big Data for Retail and Property
As interesting as Big Data can be for finding patterns in the past, its biggest promise for security lies in being able to predict the future.
December 1, 2013
Columns
Back to TopSecuring Schools After Sandy Hook
Last year, on December 14, 20-year-old Adam Lanza fatally shot 20 young children and six adults at Sandy Hook Elementary School in Newtown, Ct.
December 1, 2013
How the Generational Security Gap Affects Security
Despite concerns about technology, clearly Americans still have a hard time unplugging.
December 1, 2013
Studying the Pros and Cons of Proprietary Wireless Surveillance
There are many examples within the technology industry of proprietary being considered better than standards-based systems.
December 1, 2013
What to Expect When Working with Cyber Cops
What your company, as a victim of a computer intrusion, should expect when working with the Feds.
December 1, 2013
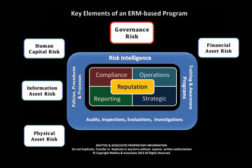
How to Keep Up With Governance Risk
Establishing and maintaining a culture across the enterprise that is based on unwavering ethical practices from the boardroom to the lowest level employee is also a key element of effective governance programs.
December 1, 2013
Get our new eMagazine delivered to your inbox every month.
Stay in the know on the latest enterprise risk and security industry trends.
SUBSCRIBE TODAY!Copyright ©2024. All Rights Reserved BNP Media.
Design, CMS, Hosting & Web Development :: ePublishing